背景:某辦公樓三層約15間辦公室(終端數約30個)有互聯網需求,樓棟綜合佈線已由房建單位實施完成,所有辦公室網線匯聚至2樓機房。機房現有華爲MA5620 電信PON網絡ONU一臺,寬帶撥號賬號3個(每條寬帶20M帶寬)。中興1800-2S多業務路由器1臺,中興5250交換機1臺。
方案1:由電信提供的三合一機頂盒3個,對應3個寬帶帳號;在交換機上劃分3個VLAN,一個VLAN對應一個寬帶帳號,實現上網。
方案2:三個寬帶賬號全部接入中興路由器,相當於一條60M的“專線”,交換機下接入所有辦公終端。方案2具體實現過程如下:
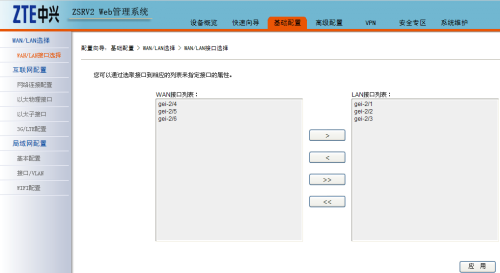
1、通過OAM口登陸中興路由器http://192.168.1.1。先選擇接口,這裏我們選擇ge-2/4~2/6爲WAN接口,作爲pppoe撥號接入。
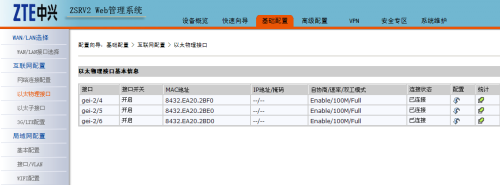
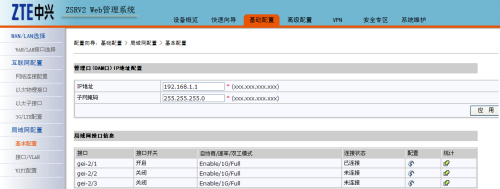
2、配置互聯網接口及局域網接口
這裏需要注意的是,在互聯網配置下以太物理接口下,mac地址必須修改爲互不相同的地址,否則同時只能有1個帳號能撥上號。
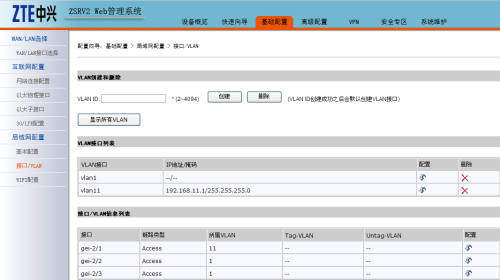
3、配置LAN接口及接口VLAN、地址
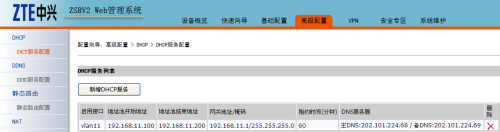
4、配置DHCP服務器
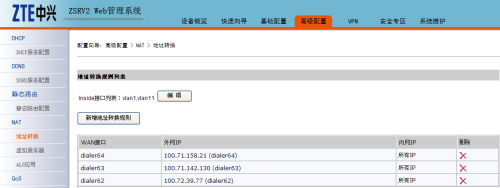
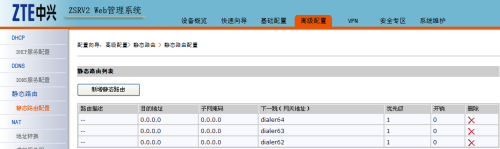
完成這些配置後,可以看到路由器自動添加了靜態路由配置,在高級配置-->NAT-->NAT轉換下可以看到3個帳號都已經撥上號獲得了公網IP地址。
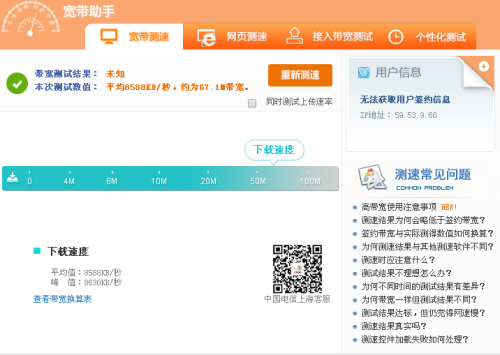
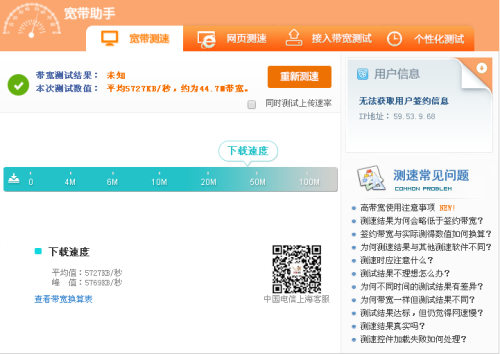
至於流量是如何分擔到3條pppoe撥號線路上的,由於技術有限,暫時還沒有原理上的驗證,只是通過簡單的測速來看下實際的效果。
以上是通過web方式來配置的,簡單直觀。配置保存後,又通過串口登陸,查看下了配置腳本如下,希望對大家有幫助。
ZXR10>en 18
Password:
ZXR10#show run
ZXR10#show running-config
!<mim>
!configuration saved at 08:03:27 Sun Mar 26 2017 by write zdb
!configuration saved at 08:03:33 Sun Mar 26 2017 by write txt
!last configuration change at 07:56:34 Sun Mar 26 2017 by admin
!</mim>
!<pm_sys>
hostname ZXR10
nvram boot-server 192.168.10.100
nvram default-gateway 192.168.10.100
nvram boot-username 123
nvram ftp-path .
!</pm_sys>
!<if-intf>
interface eth_cellular-2/1
$
interface gei-2/1
no shutdown
switch attribute enable
$
interface gei-2/2
switch attribute enable
$
interface gei-2/3
switch attribute enable
$
interface gei-2/4
description p4
no shutdown
interface mac-address 8432.ea20.2bf0
$
interface gei-2/5
description p1
no shutdown
interface mac-address 8432.ea20.2be0
$
interface gei-2/6
description p2
no shutdown
$
interface spi-2/1
$
interface mgmt_eth
ip address 192.168.1.1 255.255.255.0
$
interface vlan1
$
interface vlan11
ip address 192.168.11.1 255.255.255.0
$
interface null1
$
interface dialer62
$
interface dialer63
$
interface dialer64
$
interface virtual_template62
mode ppp
$
interface virtual_template63
mode ppp
$
interface virtual_template64
mode ppp
$
!</if-intf>
!<switchvlan>
switchvlan-configuration
interface gei-2/1
switchport access vlan 11
$
vlan 1
$
vlan 11
$
$
!</switchvlan>
!<ipv4-acl>
ipv4-access-list web_dypat_gei-2/5
rule 1 permit any
$
ipv4-access-list web_dypat_gei-2/6
rule 1 permit any
$
ipv4-access-list web_fwacl_trust2untrust
$
ipv4-access-list web_fwacl_untrust2trust
$
ipv4-access-list web_dypat_gei-2/4
rule 1 permit any
$
!</ipv4-acl>
!<ippool>
ip pool web_ds_vlan11
range 192.168.11.100 192.168.11.200 255.255.255.0
$
!</ippool>
!<system-user>
system-user
authorization-template 1
bind aaa-authorization-template 2001
local-privilege-level 15
$
authentication-template 1
bind aaa-authentication-template 2001
$
user-name admin
bind authentication-template 1
bind authorization-template 1
password encrypted 5e369850fc0db7485326620602a5e33d0ad4cf5050b393a682eabf186
9aa761a
$
$
!</system-user>
!<dhcp>
ip dhcp pool web_ds_vlan11
ip-pool web_ds_vlan11
default-router 192.168.11.1
dns-server 202.101.224.68
dns-server 202.101.224.69
$
ip dhcp policy web_ds_vlan11 1
dhcp-pool web_ds_vlan11
$
dhcp
enable
interface vlan11
mode server
policy web_ds_vlan11
$
$
!</dhcp>
!<cgn>
cgn
cgn-pool web_portpat_gei-2/4 poolid 1997 mode pat
section 1 interface dialer62
$
cgn-pool web_portpat_gei-2/6 poolid 1998 mode pat
section 1 interface dialer63
$
cgn-pool web_portpat_gei-2/5 poolid 1999 mode pat
section 1 interface dialer64
$
domain web_pat_common 4000 type sr ipv4-issued
dynamic source rule-id 1998 ipv4-list web_dypat_gei-2/4 permit pool web_port
pat_gei-2/4 dialer62
dynamic source rule-id 1999 ipv4-list web_dypat_gei-2/6 permit pool web_port
pat_gei-2/6 dialer63
dynamic source rule-id 2000 ipv4-list web_dypat_gei-2/5 permit pool web_port
pat_gei-2/5 dialer64
$
subscriber ipv4 public subscriber-id 4000 nat-domain 4000
interface vlan1
interface vlan11
$
$
!</cgn>
!<aaa>
aaa-authentication-template 2001
aaa-authentication-type local
$
aaa-authorization-template 2001
aaa-authorization-type local
$
!</aaa>
!<ppp>
ppp
interface virtual_template62
ppp chap hostname 0791012876710
ppp chap password encrypted vZikWOTiwThR7mH1s6CDXg==
ppp ipcp dns request
ppp pap sent-username 0791012876710 password encrypted vZikWOTiwThR7mH1s6CDX
g==
$
interface virtual_template63
ppp chap hostname 0791012882830
ppp chap password encrypted OW1o1wJipoS9448QrHEPeA==
ppp ipcp dns request
ppp pap sent-username 0791012882830 password encrypted OW1o1wJipoS9448QrHEPe
A==
$
interface virtual_template64
ppp chap hostname 0791012882901
ppp chap password encrypted zUjuXmcL4A7tFvhbPTdjsg==
ppp ipcp dns request
ppp pap sent-username 0791012882901 password encrypted zUjuXmcL4A7tFvhbPTdjs
g==
$
$
!</ppp>
!<arp>
arp
interface vlan1
periodic freearp 30
$
interface vlan11
periodic freearp 30
$
$
!</arp>
!<alarm>
logging file default almlog
accept on
$
logging file default cmdlog
buffer 1000
$
logging file default srvlog
accept on
interval 10
$
logging snmp
accept on
match cmdlog
$
!</alarm>
!<static>
ip route 0.0.0.0 0.0.0.0 dialer64
ip route 0.0.0.0 0.0.0.0 dialer63
ip route 0.0.0.0 0.0.0.0 dialer62
!</static>
!<firewall>
firewall
zone security web_fw_trustzone priority 254
$
zone security web_fw_untrustzone priority 250
$
zone-pair security web_fw_zonepair2untrust source web_fw_trustzone destination
web_fw_untrustzone
ipv4-access-group web_fwacl_trust2untrust
$
zone-pair security web_fw_zonepair2trust source web_fw_untrustzone destination
web_fw_trustzone
ipv4-access-group web_fwacl_untrust2trust
$
$
!</firewall>
!<SDC>
sdc
virtual-template interface virtual_template64
bind interface gei-2/5
$
virtual-template interface virtual_template63
bind interface gei-2/6
$
virtual-template interface virtual_template62
bind interface gei-2/4
$
dialer interface dialer64
auto-redial enable
member priority high virtual_template64
$
dialer interface dialer63
auto-redial enable
member priority high virtual_template63
$
dialer interface dialer62
auto-redial enable
member priority high virtual_template62
$
$
!</SDC>
ZXR10#