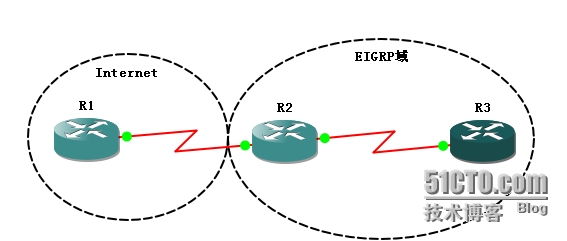
如何將默認路由下放到EIGRP域
預配:
R1:
interface s1/0
ip address 12.1.1.1 255.255.255.0
no shut
interface loopback 0
ip address 1.1.1.1 255.255.255.0
no shut
R2:
interface s1/1
ip address 12.1.1.2 255.255.255.0
no shut
interface s1/0
ip address 23.1.1.2 255.255.255.0
no shut
interface loopback 0
ip address 2.2.2.2 255.255.255.0
no shut
R3:
interface s1/1
ip address 23.1.1.3 255.255.255.0
no shut
interface loopback 0
ip address 3.3.3.3 255.255.255.0
no shut
配置EIGRP域
R1:
router eigrp 90
eigrp router-id 1.1.1.1
network 12.1.1.0 0.0.0.255
no auto-summary
R2:
router eigrp 90
eigrp router-id 2.2.2.2
network 12.1.1.0 0.0.0.255
network 23.1.1.0 0.0.0.255
no auto-summary
R3:
router eigrp 90
eigrp router-id 3.3.3.3
network 23.1.1.0 0.0.0.255
no auto-summary
1、重分佈默認路由
R1:
ip route 0.0.0.0 0.0.0.0 12.1.1.2或s1/0
router eigrp 90
redistribute static 重分佈靜態路由
2、宣告0.0.0.0 網絡
這裏的默認路由必須是以退出接口的配置參數
ip route 0.0.0.0 0.0.0.0 s1/0
router eigrp 90
network 0.0.0.0
3、使用ip default-network
命令如下:
ip default-network 12.0.0.0
ip route 12.0.0.0 255.0.0.0 s1/0創建需要通告的類似直連網絡的靜態路由,且只能以退出接口
router eigrp 90
network 12.0.0.0
添加ip default-network是添加默認路由,而需要通告該默認路由,沒有類似的直連網絡
所以需要創建一個類似於直連接口的靜態路由
4、在接口中將彙總成默認路由
R1:
interface s1/0
ip summary-address eigrp 90 0.0.0.0 0.0.0.0
auto-summary:
1、在主類網絡邊界上自動彙總
2、手工彙總:在接口下作手工彙總,是路由傳播方向的Out方向
當彙總路由的所有明細條目down後,彙總路由才消失
當彙總的明細路由是多條不同metric的時候,彙總選最小值的metric
EIGRP的三種管理距離:
內部EIGRP路由是90
外部EIGRP路由是170
EIGRP彙總路由是50
驗證16次重傳機制:
配置:
R1
interface f0/0
ip address 12.1.1.1 255.255.255.0
no shut
interface lo0
ip address 1.1.1.1 255.255.255.0
no shut
router eigrp 90
eigrp router-id 1.1.1.1
network 12.1.1.0 0.0.0.255
network 1.1.1.0 0.0.0.255
no auto-summary
R2:
interface f0/1
ip address 12.1.1.2 255.255.255.0
no shut
interface l0
ip address 2.2.2.2 255.255.255.0
no shut
router eigrp 90
eigrp router-id 2.2.2.2
network 12.1.1.0 0.0.0.255
network 2.2.2.0 0.0.0.255
no auto-summary
設想這樣一個場景:
當R2發送hello包給R1的時候,採用一些措施不讓R1回覆hello包給R2,從而導致重傳的開始
開始我採用這個ACL規則:在R1上
ip access-list extended 100
deny eigrp any host 12.1.1.1
permit ip any any
interface f0/0
ip access-group 100 in
可是不起作用哦!爲什麼呢?
我們只知道,它們發送hello包的時候,目的IP地址是224.0.0.10
所以這個ACL規則根本抓不到包,規則不起作用的哦
修改如下
ip access-list extended 100
deny eigrp any host 224.0.0.10
permit ip any any
就可以了
Mar 1 00:06:59.943: AS 90, Flags 0x0, Seq 0/0 idbQ 0/0 iidbQ un/rely 0/0
*Mar 1 00:06:59.975: EIGRP: Sending UPDATE on FastEthernet0/1 nbr 12.1.1.1, retry 16, RTO 5000
*Mar 1 00:06:59.975: AS 90, Flags 0x1, Seq 12/0 idbQ 0/0 iidbQ un/rely 0/0 peerQ un/rely 0/2
R2#un all
*Mar 1 00:07:02.855: EIGRP: Received HELLO on FastEthernet0/1 nbr 12.1.1.1
*Mar 1 00:07:02.859: AS 90, Flags 0x0, Seq 0/0 idbQ 0/0 iidbQ un/rely 0/0 peerQ un/rely 0/2
R2#un all
*Mar 1 00:07:04.479: EIGRP: Sending HELLO on FastEthernet0/1
*Mar 1 00:07:04.479: AS 90, Flags 0x0, Seq 0/0 idbQ 0/0 iidbQ un/rely 0/0
*Mar 1 00:07:04.699: EIGRP: Sending HELLO on Loopback0
*Mar 1 00:07:04.699: AS 90, Flags 0x0, Seq 0/0 idbQ 0/0 iidbQ un/rely 0/0
*Mar 1 00:07:04.703: EIGRP: Received HELLO on Loopback0 nbr 2.2.2.2
*Mar 1 00:07:04.707: AS 90, Flags 0x0, Seq 0/0 idbQ 0/0
*Mar 1 00:07:04.707: EIGRP: Packet from ourselves ignored
*Mar 1 00:07:04.975: EIGRP: Retransmission retry limit exceeded
*Mar 1 00:07:04.975: EIGRP: Sending HELLO on FastEthernet0/1
*Mar 1 00:07:04.975: AS 90, Flags 0x0, Seq 0/0 idbQ 0/0 iidbQ un/rely 0/0
*Mar 1 00:07:04.983: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 90: Neighbor 12.1.1.1 (FastEthernet0/1) is down: retry limit exceeded
看到了吧,16次後,鄰居關係down掉
EIGRP DUAL算法:
successor:指的的是路由器哦
最優路由的下一跳路由器
FS:指的也是路由器
次優路由的下一跳路由器
FS的條件:
次優路由的AD必須小於最優路由FD,就可以成爲FS
如果successor沒有了,將啓用FS,如果沒有FS,就發送查詢給鄰居
EIGRP 負載均衡
查看負載均衡條目,最大6條 show ip protocols
非等價負載均衡:
successor的FD*varian>FS的FD就可以了
EIGRP接口的利用率:默認百分之五十
ip bandwidth-percent eigrp 90 200 百分之200,結合bandwidth來使用
一般在應用於WAN鏈路的情況下使用
查詢過程:
1、在路由丟失,無FS
2、發送給其他鄰居,除了successor接口
3、如果鄰居沒有該路由信息,查詢往其他鄰居擴散
會遇到SIA狀態,也就是卡在active狀態,默認3分鐘沒有收到回覆,重置鄰居
timer active-time 3這個就是設置SIA時間,默認在進程下配置
如何限制查詢包的擴散:
1、彙總
彙總後的子網掩碼不一樣,當查詢報文來了後,將沒有該路由,直接回復reply
2、EIGRP STUB
配置stub的路由器主動發送帶有stub標識的報文
而丟失路由的路由器不會發查詢報文給stub路由器
router eigrp 90
eigrp stub
模擬這個實驗
R1:
interface f0/0
ip address 12.1.1.1 255.255.255.0
no shut
interface l0
ip address 1.1.1.1 255.255.255.0
no shut
router eigrp 90
eigrp router-id 1.1.1.1
network 12.1.1.0 0.0.0.255
network 1.1.1.0 0.0.0.255
no auto-summary
R2:
interface f0/1
ip address 12.1.1.2 255.255.255.0
no shut
interface l0
ip address 2.2.2.2 255.255.255.0
no shut
router eigrp 90
eigrp router-id 2.2.2.2
network 12.1.1.0 0.0.0.255
network 2.2.2.0 0.0.0.255
no auto-summary
當R2down掉loopback0口時候
R2會發送query報文給R1
debug eigrp packets query 可以看到發送的query報文
debup eigrp packets hello 可以看到發送的hello報文
show ip eigrp neighbors detail
R2#show ip eigrp neighbors detail
IP-EIGRP neighbors for process 90
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 12.1.1.1 Se1/0 13 00:06:38 37 222 0 39
Version 12.4/1.2, Retrans: 0, Retries: 0, Prefixes: 1
Stub Peer Advertising ( CONNECTED SUMMARY ) Routes
Suppressing queries
所以R2是不會發送query報文給R1的
eigrp stub的默認參數有connected summary
如果配置成stub,只會發直連路由和彙總給鄰居
EIGRP的認證:只支持MD5認證
基於接口的認證:
key chain R2 僅本地有效
key 1
key-string cisco
interface f0/0
ip authentication key-chain eigrp 90 R2
ip authentication mode eigrp 90 md5
被動接口passive-interface,用於環回口,不收發認hello報文,但是該環回口會被通告
偏移列表:用來修改metric值
先用ACL來抓路由
offset-list acl名 in 4 路由進程中 入接口
過濾路由:
原理是這樣的,如果需要過濾掉EIGRP拓撲表信息,就可以過濾掉路由。
總共有兩個方向,in方向是接受到的EIGRP拓撲信息進行過濾,out方向是發送出去的EIGRP拓撲
信息進行路由過濾。
配置信息重新來過:
R1:
interface e0/0
ip add 10.10.12.1 255.255.255.0
no shut
interface lo0
ip add 1.1.1.1 255.255.255.0
ip add 172.16.0.1 255.255.255.0 secondary
ip add 172.16.1.1 255.255.255.0 secondary
ip add 172.16.2.1 255.255.255.0 secondary
no shut
router eigrp 90
eigpr router-id 1.1.1.1
network 10.10.12.0 0.0.0.255
network 1.1.1.0 0.0.0.255
network 172.16.0.0 0.0.0.255
network 172.16.1.0 0.0.0.255
network 172.16.2.0 0.0.0.255
R2:
interface e0/1
ip add 10.10.12.2 255.255.255.0
no shut
interface e0/0
ip add 10.10.23.2 255.255.255.0
no shut
interface l0
ip add 2.2.2.2 255.255.255.0
no shut
router eigrp 90
eigrp router-id 2.2.2.2
network 10.10.12.0 0.0.0.255
network 10.10.23.0 0.0.0.255
network 2.2.2.0 0.0.0.255
router eigrp 90
eigrp router-id 2.2.2.2
network 10.10.12.0 0.0.0.255
network 10.10.23.0 0.0.0.255
network 2.2.2.0 0.0.0.255
R3:
interface e0/1
ip add 10.10.23.3 255.255.255.0
no shut
interface l0
ip add 3.3.3.3 255.255.255.0
no shut
router eigrp 90
eigrp router-id 3.3.3.3
network 10.10.23.0 0.0.0.255
network 3.3.3.0 0.0.0.255
在R2上,show ip route
R2(config-router)#do show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
1.0.0.0/24 is subnetted, 1 subnets
D 1.1.1.0 [90/409600] via 10.10.12.1, 00:32:35, Ethernet0/1
2.0.0.0/24 is subnetted, 1 subnets
C 2.2.2.0 is directly connected, Loopback0
3.0.0.0/24 is subnetted, 1 subnets
D 3.3.3.0 [90/409600] via 10.10.23.3, 00:30:24, Ethernet0/0
172.16.0.0/24 is subnetted, 3 subnets
D 172.16.0.0 [90/409600] via 10.10.12.1, 00:00:07, Ethernet0/1
D 172.16.1.0 [90/409600] via 10.10.12.1, 00:32:35, Ethernet0/1
D 172.16.2.0 [90/409600] via 10.10.12.1, 00:32:37, Ethernet0/1
10.0.0.0/24 is subnetted, 2 subnets
C 10.10.12.0 is directly connected, Ethernet0/1
C 10.10.23.0 is directly connected, Ethernet0/0
我想過濾掉172.16.0.0 255.255.255.0 這條路由條目
R2:
access-list 1 deny 172.16.0.0 0.0.0.255
access-list 1 permit any
router eigrp 90
distribute-list 1 in e0/1
R2(config-router)#do show ip route eigrp
1.0.0.0/24 is subnetted, 1 subnets
D 1.1.1.0 [90/409600] via 10.10.12.1, 00:36:51, Ethernet0/1
3.0.0.0/24 is subnetted, 1 subnets
D 3.3.3.0 [90/409600] via 10.10.23.3, 00:34:39, Ethernet0/0
172.16.0.0/24 is subnetted, 2 subnets
D 172.16.1.0 [90/409600] via 10.10.12.1, 00:36:51, Ethernet0/1
D 172.16.2.0 [90/409600] via 10.10.12.1, 00:36:51, Ethernet0/1
過濾掉這條172.16.0.0 255.255.255.0了哦!
第二種方法就是使用前綴列表
ip prefix-list test permit 172.16.1.0/24
router eigrp 90
distribute-list prefix test in e0/1
那麼這樣達到的效果是什麼樣的呢?
R2(config-router)#do show ip route eigrp
3.0.0.0/24 is subnetted, 1 subnets
D 3.3.3.0 [90/409600] via 10.10.23.3, 00:56:46, Ethernet0/0
172.16.0.0/24 is subnetted, 1 subnets
D 172.16.1.0 [90/409600] via 10.10.12.1, 00:58:58, Ethernet0/1
呵呵,看着效果,本來想過濾掉172.16.1.0/24這條路由,說明是放行172.16.1.0/24這條路由
ip prefix-list test deny 172.16.1.0/24
ip prefix-list test permit 0.0.0.0/0 le 32
router eigrp 90
distribute-list prefix test in e0/1
以上兩種方法,過濾動作時通過deny來實現的
第三種方法使用route-map
access-list 1 deny 172.16.0.0 0.0.0.255
access-list 1 permit any
route-map test permit 10
match ip address 1
router eigrp 90
distribute-list route-map test in e0/1
這裏的拒絕動作還是體現在ACL的deny上,暈啊!
還可以這樣的哦
access-list 1 permit 172.16.0.0 0.0.0.255
route-map test deny 10
match ip address 1
route-map test permit 20
exit
router eigrp 90
distribute-list route-map test in e0/1
也就是說,過濾的動作也可以體現在route-map的deny動作上,記得哦
它有默認的deny any的動作