DNS相關配置
dig -t NS|MX|A NAME
dig -x IP 反向解析
IXFR增量區域傳送
AXFT完全區域傳送
dig -t IXFR=2013040202 mageedu.com (做這個之前需要更改對區域數據進行增加一條數據和更改計數)
dig -t axfr mageedu.com
allow-recursion { };允許遞歸的客戶端
allow-query { };允許查詢的客戶端
allow-transfer { };允許傳送的客戶端
/etc/named.conf 可以使用configtest測試
/etc/rndc.key祕鑰文件
/etc/rndc.conf配置文件
/var/named/區域數據文件,需要創建
named-checkconf
named-checkzone
dig 客戶端工具
dig -t NS.獲取根域服務器(必須能上網)
53/udp
53/tcp 從服務器同步數據時使用tcp協議53端口
953/tcp,rndc
區域定義:
zone "ZONE NAME" IN {
type master|slave|hint|forward;
};
若是主區域還需要配置:
file "區域數據文件";
若是從區域:
file "區域數據文件";
masters {masters1_ip;};
netstat -utnpl
首先安裝bind文件
yum install bind
DNS的簡單設定
Yum install bind -y
1. 端口號的查詢
[root@student116 ~]# netstat -antlpe | grep named
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 25 40524 2422/named
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 25 40519 2422/named
tcp6 0 0 ::1:953 :::* LISTEN 25 40525 2422/named
tcp6 0 0 ::1:53 :::* LISTEN 25 40521 2422/named
2.systemctl start named
3.vim /etc/named.conf
修改下列:
listen-on port 53 { any; };
allow-query { any; };
dnssec-validation no;
添加--> forwarders {172.25.254.250;}; #能連接到外網的ip地址
例:dig www.baidu.com
#################客戶端###################
1.vim /etc/resolv.com
nameserver 172.25.254.139 ######使其指向提供服務的dns服務器
2.dig www.baidu.com ######會看到139主機提供解析
##################DNS相關實驗#####################################
服務器ip:172.25.39.10
172.25.254.139
客戶端ip:172.25.39.11
DNS正向解析
在之前的步驟完成後
1.vim /etc/named.rfc1912.zones
2.複製6行並修改:
zone "westos.com" IN {
type master;
file "westos.com.zone"; ######自己維護的域###
allow-update { none; };
};
3.cd /var/named
4.cp -p named.localhost westos.com.zone
5.vim westos.com.zone
$TTL 1D
@ IN SOA dns.westos.com. root. ( ######和自己維護的域相同
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns.westos.com. ####和自己維護的域相同
dns A 172.25.254.139 ####dns域名
www A 172.25.254.1 ####隨意
6.systemctl restart named
.在客戶端 dig www.westos.com
結果:
[root@student16 kiosk]# dig www.westos.com
#################################################
1.修改:
vim /var/named/westos.com.zone
$TTL 1D
@ IN SOA dns.westos.com. root. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns.westos.com.
dns A 172.25.254.139
www CNAME bbs.westos.com. ###########修改部分
bbs A 172.25.254.111 ###########修改部分
bbs A 172.25.254.112 ###########修改部分
2.在客戶端dig www.westos.com
DNS的反向解析
1.vim /etc/named.rfc1912.zones
增加內容
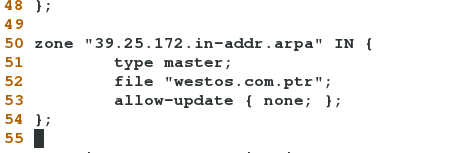
zone "254.25.172.in-addr.arpa" IN {
type master;
file "westos.comNaNr";
allow-update { none; };
};
2.創建westos.com文件
1.cd /var/named/
2.cp -p wetos.com.zone westos.com.ptr
3.vim westos.com.ptr
修改如下:
$TTL 1D
@ IN SOA dns.westos.com. root. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns.westos.com.
dns A 172.25.254.139
199 PTR www.westos.com.
234 PTR bbs.westos.com.
2.systemctl resatrt named
############################在客戶端驗證################################
1.dig -x 172.25.39.199
DNS雙向解析(內外網的不同解析)
1.vim /etc/named.conf
註釋以下內容
並加入如下內容:
view localhost {
match-clients {localhost;};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
};
view internet {
match-clients { any;};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1913.zones";
};
2.cd /etc/named/
3. cp -p named.rfc1912.zones named.rfc1912.zones.inter
4.vim named.rfc1912.zones.inter
增加內容:
zone "westos.com" IN {
type master;
file "westos.com.inter";
allow-update { none; };
};
5.systemctl restart named
建立westos.com.inter文件:
1.cd /var/named
2.cp -ap westos.com.zone westos.com.inter
3.vim westos.com.inter #########
修改如下:
$TTL 1D
@ IN SOA dns.westos.com. root. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns.westos.com.
dns A 172.25.39.139
www A 192.168.1.1 #########此處添加要訪問的外網地址###
4.systemctl restart named
###########################驗證結果####################
注意將服務器本身的dns指向自己;客戶端的dns指向服務器
1.在服務器本身:
dig www.westos.com 結果爲:172.25.254.*
2.在客戶端爲:
dig www.westos.com 結果爲:192.168.1.*
DNS集羣
#################從服務器的設定#################
主服務器:10(desktop) ---> "master"; 輔助服務器:11(server) --> slave
1.安裝dns服務:
2.systemctl restart named;systmectl stop firewalld
3.vim /etc/resolv.conf ---> nameserver 172.25.39.11 ;改爲自己的ip;
4.修改從服務器的配置:
vim /etc/named.conf
修改:listen-on port 53 { any; };
allow-query { any; };
dnssec-validation no;
5.vim /etc/named.rfc1912.zones
複製並修改:
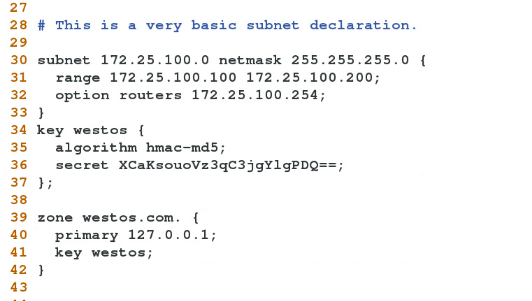
zone "westos.com" IN { ##########維護的域要相同
type slave;
masters {172.25.39.10;}; ##########指向10,說明10是他的主服
file "slaves/westos.com.zone"; ##########指出路徑
allow-update { none; };
};
6.systemctl restart named
7.dig www.westos.com ###查看內容
######主服務器的配置修改##################################
1.vim /etc/named.rfc1913.zone
修改並添加:
zone "westos.com" IN {
type master;
file "westos.com.zone";
allow-update { none; };
allow-transfer {172.25.39.11;}; ########添加上輔助dns服務器的ip;
also-notify {172.25.39.11;};
};
2.systemctl restart named;
systemctl stop firewalld;
3.修改 /var/named/westos.com.zone
從 bbs A 172.25.254.222 ---> 172.25.254.255 時 ,要注意每次修改 " 2016251601" ; serial
改變一次解析地址,改變一次serial,保存退出,刷新後在從服務器上dig www.westos.com 時會看到新的已更改的ip地址。
DNS更新
#########################主服務器部分######################
1.vim /etc/named.rfc1913.com.zone
zone "westos.com" IN {
type master;
file "westos.com.zone";
allow-update { 172.25.39.11;}; ##將 none --> 指定更新的從服務器的ip()172.25.254.11;
allow-transfer {172.25.39.11;};
also-notify {172.25.39.11;};
};
2.cd /var/named
3.getsebool -a | grep named
[root@foundation116 doc]# getsebool -a | grep named
named_tcp_bind_http_port --> off
named_write_master_zones --> on
4.setsebool -P named_write_master_zones on
5.cd /var/named ;
ll -d ;
chmod g+w /var/named
6.cp -p westos.com.zone /mnt/ ##備份,爲後續實驗準備,因爲從服務器更新會改變該文件內容
####################主服務器配置完成##########
#########從服務器的改變####################
向主服務器申請更新主服務器的dns的域名和ip;
服務器的dns的域名和ip就是其他從服務器的dns的域名
和ip;因爲他們是集羣關係!
更新完畢之後可在主服務器的 /var/named/westos.com.zone; 中發現:會有從服務器更新的dns域名和ip;
實驗:
然後dig www.westos.com測試,則不會顯示域名和ip
添加
1.[root@slave mnt]# nsupdate
> server 172.25.39.10 ##########主服務器的ip
> update add test.westos.com 86400 A 172.25.39.111 ##########新的dns域名和ip
> send ##########發送命令
> quit ##########推出
2.dig test.westos.com
[root@slave mnt]# dig test.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> test.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 62064
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;test.westos.com.INA
;; ANSWER SECTION:
test.westos.com.86400INA172.25.39.111 #######自己申請的域名和ip(test.westos.com;172.25.39.111)
;; AUTHORITY SECTION:
westos.com.86400INNSdns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com.86400INA172,25,44.10
;; Query time: 1 msec
;; SERVER: 172.25.39.10#53(172.25.39.10)
;; WHEN: Sat Aug 15 11:33:09 CST 2015
;; MSG SIZE rcvd: 94
3.此爲驗證成功!
4.可在主服務器的 /var/named/westos.com.zone 中查看更新的dns的域名和ip;
DNS的加密更新
####################主服務器配置########################
1.rm -fr /var/named/westos.com.zone ;westos.com.inter,jnl;
2.cp -p /mnt/westos.com.zone /var/named/
3.cat /etc/rndc.key
key "rndc-key" {
algorithm hmac-md5;
secret "F1qtiCvSQ+itJqgSdG5uqw==";
};
4. cd /mnt
dnssec-keygen -a HMAC-MD5 -b 128 -n HOST westos
###生成加密密碼########
5.[root@foundation116 mnt]# cat Kwestos.+157+25331.private
Private-key-format: v1.3
Algorithm: 157 (HMAC_MD5)
Key: QJL7Jx0/H6UGu/H2iI9jdg== ###########對密碼:QJL7Jx0/H6UGu/H2iI9jdg== ##進行復制
Bits: AAA=:
Created: 20150815071748
Publish: 20150815071748
Activate: 20150815071748
6.cp -p /etc/rndc.key /etc/westos.key
7.vim /etc/westos.key
key "westos" { #######改名字#####
algorithm hmac-md5;
secret "QJL7Jx0/H6UGu/H2iI9jdg=="; ####粘貼之前複製的密碼
};
8.vim /etc/named.conf
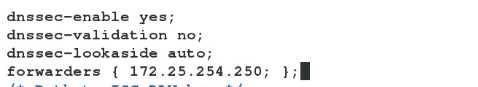
添加: dnssec-enable yes;
dnssec-validation no;
dnssec-lookaside auto;vim
forwarders {172.25.254.250;};
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
include "/etc/westos.key"; #########添加的語句###
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
9.vim /etc/named.rfc1913.zones
zone "westos.com" IN {
type master;
file "westos.com.inter";
allow-update { key westos; }; ########修改爲key westos ;
allow-transfer {172.25.39.11;};
also-notify {172.25.39.11;};
10.systemctl restart named
11.cd /mnt;
scp Kwestos.+157+41687.* [email protected]:/mnt
###############從服務器################
1.cd /mnt
2.[root@slave mnt]# nsupdate -k Kwestos.+157+53788.private
> server 172.25.254.139 ##主服務器ip
> update add test.westos.com 86400 A 172.25.254.123 ###新的域名和ip
> send
> quit
[root@slave mnt]# dig test.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> test.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 9145
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;test.westos.com.INA
;; ANSWER SECTION:
test.westos.com.86400INA172.25.254.123
;; AUTHORITY SECTION:
westos.com.86400INNSdns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com.86400INA192.168.1.1
;; Query time: 1 msec
;; SERVER: 172.25.254.116#53(172.25.254.116)
;; WHEN: Sat Aug 15 16:03:05 CST 2015
;; MSG SIZE rcvd: 94
###################驗證完畢#####################
DNS動態解析(ddns)
#####主服務器配置##############
基於dns加密更新配置的基礎上
配置DHCP服務
yum install dhcp -y
systemctl stop firewalld
systemctl start dhcpd
cp /usr/share/doc/dhcp-4.2.5/dhcpd.conf.example /etc/dhcp/dhcpd.conf
vim /etc/dhcp/dhcpd.conf
刪除37行以下,並刪除27行,然後做以下配置的編寫
7 option dimian-name "westos.com"; ##要填寫的本機域名
8 option dimian-name-severs 172.25.254.139 ###dns地址
增加語句:ddns-update-style interim
30 subnet 172.25.39.0 netmask 255.255.255.0 ##網段和子網掩碼
31 range 172.25.39.100 172.25.39.150 ###dhcp分配ip的範圍
32 option routers 172.25.254.139 #網關
密碼信息就是生成的密碼文件中的信息,不要寫錯
zone 後面的名字就是在dns配置文件中寫入的,域名
cd /var/named
rm -fr westos.com.zone westos.com.zone.jnl ##刪除原來的zone配置文件
cp -p /mnt/westos.com.zone . ####將之前備份的/westos.com.zone複製到當前位置。或者重新寫一個westos.com.zone
systemc restart named
systemctl retstart dhcpd.service
#############從服務器##############
systemctl stop firewalld
將ip改成動態獲取
vim /etc/sysconfig/network-script/eth0
更改配置後
systemctl restart network
ifconfig
vim /etc/resolv.comf
確認dns指向服務器的ip
並且域名必須與主服務器一置(本實驗域名爲westos.com)
域名不一致則需更改主機名(hostnamectl set-hostname client.westos.com)
sysetmctl restart named
dig client.westos.com 測試
取此時解析的ip則爲當前客戶主機所獲的動態ip
本次所有實驗在更改完配置文件後一定要重啓服務。