Docker的組成
Docker 是Docker.lnc公司開源的一個基於LXC技術之上構建的Container容器引擎,源代碼託管在GitHub上,基於Go語言並遵從Apache2.0協議開源。
Docker是通過內核虛擬化技術(namespaces及cgroups等)來提供容器的資源隔離與安全保障等。
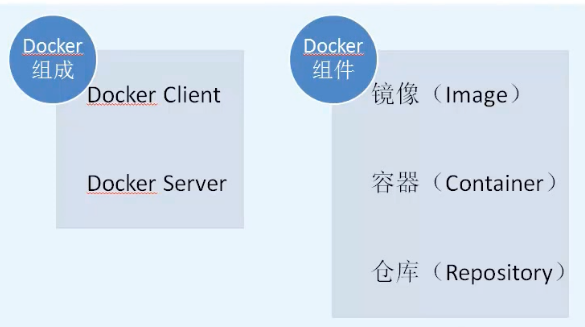
Docker由Docker Server和 Docker Client組成。
Docker組件分爲:鏡像(Image)、容器(Container)和倉庫(Repository)。Docker與Kvm的區別和優勢:
1、更快捷的交付部署: Docker 可以快速創建容器,快速迭代應用程序,並讓整個過程全程可見,使團隊中的其他成員更容易理解應用程序是如何創建和工作的。 Docker 容器很輕很快!容器的啓動時間是秒級的,大量地節約開發、測試、部署的時間。
2、更高效的虛擬化:Docker 容器的運行不需要額外的 hypervisor 支持,它是內核級的虛擬化,因此可以實現更高的性能和效率。
3、更輕鬆的遷移和擴展:ocker 容器幾乎可以在任意的平臺上運行,包括物理機、虛擬機、公有云、私有云、個人×××、服務器等。這種兼容性可以讓用戶把一個應用程序從一個平臺直接遷移到另外一個。
4、更簡單的管理:就可以替代以往大量的更新工作。所有的修改都以增量的方式被分發和更新,從而實現自動化並且高效的管理。
5、跟Kvm的區別:
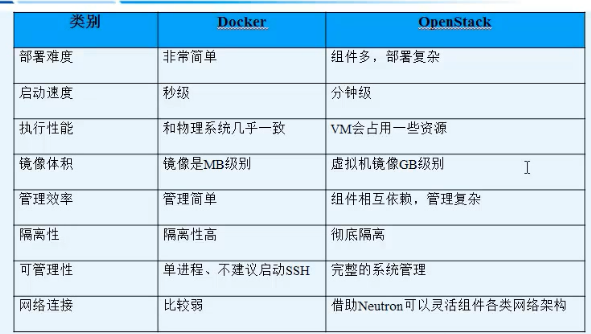
Docker與openstack的對比
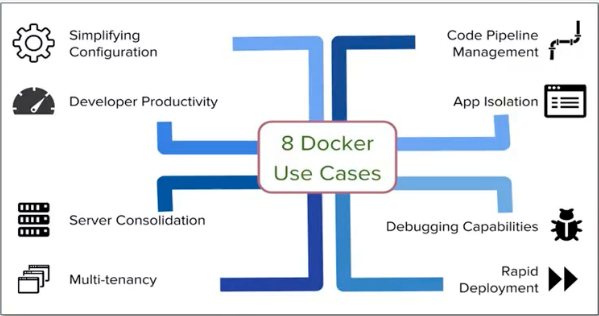
Docker能幹什麼
Docker的侷限性
1、LXC是基於cgroup等linux kernel功能的,因此container的guest系統只能是linux base的。
2、Docker的隔離性跟KVM等的虛擬化相比還是有些欠缺,所有container公用一部分的運行庫。
3、container隨着用戶進程的停止而銷燬,container中的log等用戶數據不便收集。
4、Docker是面向應用的,其終極目標是構建PAAS平臺,而現有虛擬機主要目的是提供一個靈活的計算資源池,是面向架構的,其終極目標是構建一個IAAS平臺,所以它不能替代傳統虛擬化解決方案。
一張圖總結Docker的使用:
Docker的安裝
準備:
mv /etc/yum.repos.d/CentOS-Base.repo /etc/yum.repos.d/CentOS-Base.repo.backup
wget http://mirrors.163.com/.help/CentOS7-Base-163.repo
ls
yum clean all
wget http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
yum makecache
安裝:
yum install docker 1.12.6(centos7系統)
centos6系統
yum install docker-io(版本最高1.7.1,建議用7)
yum install device-mapper-event-libs
關閉selinux
vim /etc/selinux/config
setenforce 0
啓動:
systemctl start docker
systemctl enable docker
配置國內鏡像站:
vim /etc/docker/daemon.json
{
"registry-mirrors": ["https://docker.mirrors.ustc.edu.cn"]
}
systemctl restart docker
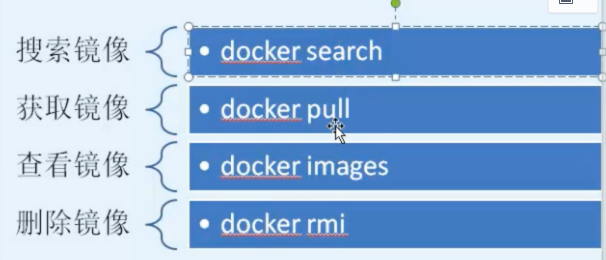
查找鏡像
docker search centos
下載鏡像
docker pull centos
查看鏡像
docker images
啓動鏡像
docker run -it -d --name nginx /bin/bash
查看ip地址
ip ad li
查看啓動的鏡像
docker ps
查看所有
docker ps -a
訪問私有鏡像站,配置:
在/etc/sysconfig/docker
添加:
ADD_REGISTRY='--add-registry 172.16.234.101:5000'
BLOCK_REGISTRY='--block-registry docker.io'
INSECURE_REGISTRY='--insecure-registry 172.16.234.101:5000'
重啓docker
再pull鏡像默認就從234.101下載了
docker pull nginx
問題解決
WARNING: IPv4 forwarding is disabled. Networking will not work.
vim /usr/lib/sysctl.d/00-system.conf
net.ipv4.ip_forward=1
systemctl restart network
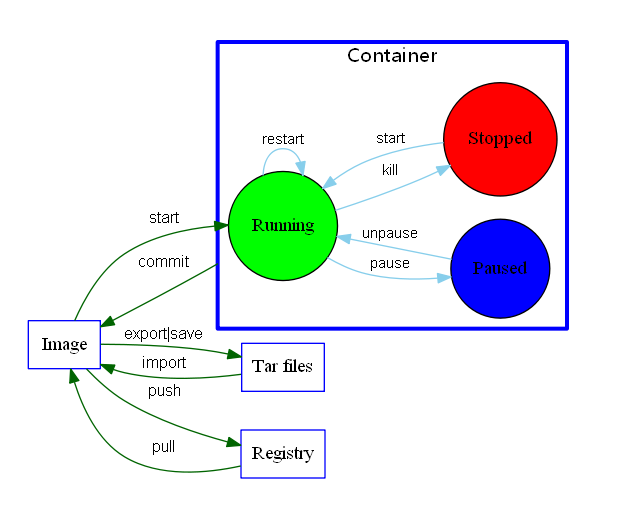
docker基本操作
導出鏡像
docker save centos > /opt/centos.tar.gz
docker save -o centos7 centos
導入鏡像
docker load centos < /opt/centos.tar.gz
docker load --input 本地鏡像
導出容器快照
docker export -o mysql-date +%Y%m%d.tar a404c6c174a2
導入容器快照
docker import my_ubuntu_v3.tar runoob/ubuntu:v4
在官方下載一個鏡像
docker pull centos
查看下載的鏡像
docker images
運行一個命令
docker run centos /bin/echo "hello"
查看當前docker運行情況
docker ps -a
運行一個命令並指定名稱
docker run --name madocker -t -i centos /bin/bash
- --name 指定名字
- -t 分配一個僞終端
- -i 保持終端打開狀態
- centos 鏡像名稱
- 命令
啓動一個容器
docker start 容器ID
進入一個容器
docker attach 容器ID
- 這種進入方式顯示是同步的,類似openstack的VNC連接方式。
- 使用exit命令,docker容器會停止運行,因爲退出了bash。
另一種進入容器的方式
nsenter -t 容器PID -u -n -i -p
- 如果沒有這個命令,需要安裝一個包,yum install util-linux -y
- -t 指定容器PID
- 獲取容器PID的方法:
1、啓動容器:docker start 容器ID
2、獲取PID:docker inspect --format "{{.State.Pid}}" 容器ID - -u 用戶空間,user namespace
- -n network namespace
- -i 進程間通信空間
- -p pid
進入容器腳本
vim ns.sh
!/bin/bash
PID=$(docker inspect --format "{{.State.Pid}}" $1)
nsenter -t $PID -u -n -i -p
chmod +x ns.sh
- ./ns.sh 容器ID 直接進入容器,並且退出時容器正常運行。
刪除一個容器
docker rm {容器ID|容器名稱}
*如果要刪除一個正在運行的容器,添加-f參數。
在運行一個命令後自動刪除容器
docker run --rm centos /bin/echo "hello"
*執行完echo命令後,該容器自動被刪除
殺死所有正在運行的容器
docker kill $(docker ps -a -q)
- -q 只列出容器ID
docker run -d --name nfs -v /data centos
手動構建一個鏡像
docker run --name mynginx -it centos
rpm -ivh http://mirrors.aliyun.com/epel/epel-release-latest-7.noarch.rpm
yum makecache
yum install vim nginx -y
vim /etc/nginx/nginx.conf
添加:
daemon off;
:wq
exit
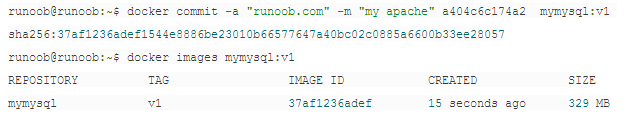
docker commit -m "my nginx" 容器id hetao/mynginx:v1
*hetao/mynginx:v1,hetao,dockerhub上的目錄,v1,版本號
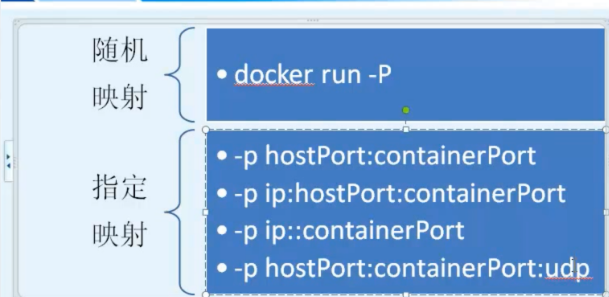
docker run -d -p 82:80 hetao/mynginx:v1 nginx
最後一個nginx爲要傳輸的命令。
使用export import導出和導入docker容器
docker export -o mysql-date +%Y%m%d.tar a404c6c174a2
docker import my_ubuntu_v3.tar runoob/ubuntu:v4
docker 網絡和存儲
docker inspect centos/容器id 列出容器centos的所有內容
docker commit
語法
docker commit [OPTIONS] CONTAINER [REPOSITORY[:TAG]]
OPTIONS說明:
-a :提交的鏡像作者;
-c :使用Dockerfile指令來創建鏡像;
-m :提交時的說明文字;
-p :在commit時,將容器暫停。
實例
將容器a404c6c174a2 保存爲新的鏡像,並添加提交人信息和說明信息。
docker file 構建鏡像
mkdir /opt/dockerfile/nginx -p
cd /opt/dockerfile
echo "dockerfile">index.html
vim Dockerfile
This docker file
VERSION 1
Author: luis
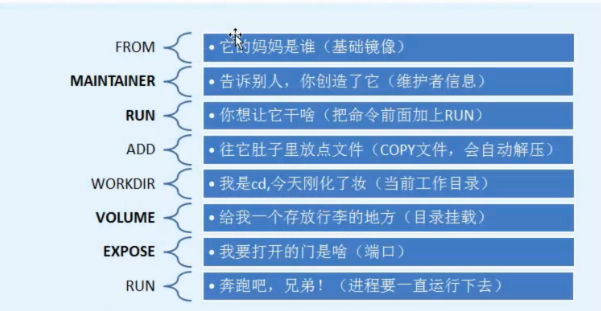
Base image
FROM centos
Maintainer
MAINTAINER hetao [email protected]
Commands
RUN rpm -ivh http://mirrors.aliyun.com/epel/epel-release-latest-7.noarch.rpm
RUN yum makecache
RUN yum install vim nginx -y
ADD index.html /usr/share/nginx/html/index.html
RUN echo "daemon off;" >>/etc/nginx/nginx.conf
EXPOSE 80
CMD ["nginx"]
centos7.3 搭建docker私庫-harbor
系統信息: Centos 7.3 64
harbor版本:1.4.0
1、安裝docker yum源(如果有epel base源,可以先備份,再下載epel和base源)
wget -O /etc/yum.repos.d/docker-ce.repo https://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
wget -O /etc/yum.repos.d/epel.repo http://mirrors.aliyun.com/repo/epel-7.repo
wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-7.repo
yum makecache fast
2、安裝docker docker-compose
yum install docker-ce docker-compose -y
systemctl start docker
systemctl enable docker
3、下載harbor在線安裝包
mkdir /data/harbor
cd /data/harbor
wget https://storage.googleapis.com/harbor-releases/release-1.4.0/harbor-online-installer-v1.4.0.tgz
tar xvf harbor-online-installer-v1.4.0.tgz
4、修改harbor.cfg文件
hostname = harbor.51cto.wang (前端域名,也可以是IP,不能是localhost/127.0.0.1)
ui_url_protocol = https (使用默認的http會導致docker login登錄不了,且不安全)
ssl_cert = /data/harbor/cert/server.crt (證書存放目錄及文件名)
ssl_cert_key = /data/harbor/cert/server.key
auth_mode = db_auth (本地數據庫認證)
harbor_admin_password = Harbor12345 (admin用戶的密碼)
project_creation_restriction = adminonly (僅管理員可以創建項目,everyone爲所有人可以創建項目)
self_registration = on (開啓自注冊功能)
5、創建證書
mkdir /data/harbor/cert && cd /data/harbor/cert
openssl req -x509 -days 3650 -nodes -newkey rsa:2048 -keyout /data/harbor/cert/server.key -out /data/harbor/cert/server.crt
(只填Common Name這一項,其他都默認回車)
Generating a 2048 bit RSA private key
...........................+++
.....................................................................................................................+++
writing new private key to ‘/data/harbor/cert/server.key‘
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
Country Name (2 letter code) [XX]:
State or Province Name (full name) []:
Locality Name (eg, city) [Default City]:
Organization Name (eg, company) [Default Company Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server‘s hostname) []:harbor.51cto.wang
Email Address []:
6、生成配置文件並啓動容器
cd /data/harbor/harbor
./install.sh
[Step 0]: checking installation environment ...
Note: docker version: 17.06.1
Note: docker-compose version: 1.9.0
[Step 1]: preparing environment ...
Clearing the configuration file: ./common/config/adminserver/env
Clearing the configuration file: ./common/config/ui/env
Clearing the configuration file: ./common/config/ui/app.conf
Clearing the configuration file: ./common/config/ui/private_key.pem
Clearing the configuration file: ./common/config/db/env
Clearing the configuration file: ./common/config/jobservice/env
Clearing the configuration file: ./common/config/jobservice/app.conf
Clearing the configuration file: ./common/config/registry/config.yml
Clearing the configuration file: ./common/config/registry/root.crt
Clearing the configuration file: ./common/config/nginx/cert/server.crt
Clearing the configuration file: ./common/config/nginx/cert/server.key
Clearing the configuration file: ./common/config/nginx/nginx.conf
Clearing the configuration file: ./common/config/log/logrotate.conf
loaded secret from file: /data/secretkey
Generated configuration file: ./common/config/nginx/nginx.conf
Generated configuration file: ./common/config/adminserver/env
Generated configuration file: ./common/config/ui/env
Generated configuration file: ./common/config/registry/config.yml
Generated configuration file: ./common/config/db/env
Generated configuration file: ./common/config/jobservice/env
Generated configuration file: ./common/config/log/logrotate.conf
Generated configuration file: ./common/config/jobservice/app.conf
Generated configuration file: ./common/config/ui/app.conf
Copied configuration file: ./common/config/uiprivate_key.pem
Copied configuration file: ./common/config/registryroot.crt
The configuration files are ready, please use docker-compose to start the service.
[Step 2]: checking existing instance of Harbor ...
Note: stopping existing Harbor instance ...
Stopping nginx ... done
Stopping harbor-jobservice ... done
Stopping harbor-adminserver ... done
Stopping registry ... done
Stopping harbor-db ... done
Stopping harbor-log ... done
Removing nginx ... done
Removing harbor-jobservice ... done
Removing harbor-ui ... done
Removing harbor-adminserver ... done
Removing registry ... done
Removing harbor-db ... done
Removing harbor-log ... done
Removing network harbor_harbor
[Step 3]: starting Harbor ...
Creating network "harbor_harbor" with the default driver
Creating harbor-log
Creating harbor-adminserver
Creating harbor-db
Creating registry
Creating harbor-ui
Creating harbor-jobservice
Creating nginx
✔ ----Harbor has been installed and started successfully.----
Now you should be able to visit the admin portal at https://harbor.51cto.wang .
For more details, please visit https://github.com/vmware/harbor .
7、登錄並推送第一個鏡像
<本地登錄>
1)登錄web,創建一個名爲test的項目
2)推送一個測試鏡像到test項目中
docker login -u admin -p Harbor123456 harbor.51cto.wang (登錄)
docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
vmware/registry-photon v2.6.2-v1.4.0 8920f621ddd1 5 weeks ago 198MB
vmware/nginx-photon v1.4.0 20c8a01ac6ab 5 weeks ago 135MB
vmware/harbor-log v1.4.0 9e818c7a27ab 5 weeks ago 200MB
vmware/harbor-jobservice v1.4.0 29c14d91b043 5 weeks ago 191MB
vmware/harbor-ui v1.4.0 6cb4318eda6a 5 weeks ago 209MB
vmware/harbor-adminserver v1.4.0 8145970fa013 5 weeks ago 182MB
vmware/harbor-db v1.4.0 c38da34727f0 5 weeks ago 521MB
task/task v2 5e45422e6d29 2 months ago 1.76GB
task/task v1 78022f6d4a90 2 months ago 1.69GB
將task:v2上傳至harbor
docker tag task/task:v2 harbor.51cto.wang/test/task:test
docker push harbor.51cto.wang/test/task:test
The push refers to a repository [harbor.51cto.wang/test/task]
196171e612cc: Pushed
test: digest: sha256:09921659d583e6e53ade0a81dc5ebccc7be6245d8a2a2c84f22539d4f64d075d size: 529
<異地登錄>
1)拷貝證書(在registry所在的服務器上操作)
mkdir -p /etc/docker/certs.d/harbor.51cto.wang
cp /data/harbor/cert/server.crt /etc/docker/certs.d/harbor.51cto.wang/ca.crt
2)在客戶端上操作
mkdir -p /etc/docker/certs.d/harbor.51cto.wang
拷貝服務端ca.crt到該目錄下
docker login -u admin -p Harbor123456 harbor.51cto.wang
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
Login Succeeded
FQA:
1、如執行腳本報錯,可分開執行,./prepare && docker-compose up -d
2、若在啓動容器過程中提示端口被佔用,可修改docker-compose.yml文件,修改端口
3、登錄時報錯:Error response from daemon: Get https://registry.niudingfeng.com/v1/users/: x509: certificate signed by unknown authority
此種情況多發生在自簽名的證書,報錯含義是簽發證書機構未經認證,無法識別。
chmod 644 /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem
cat /data/harbor/cert/server.crt >>/etc/pki/tls/certs/ca-bundle.crt
chmod 444 /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem
systemctl restart docker
參考文檔:
http://www.bubuko.com/infodetail-1944996.html
https://vmware.github.io/harbor/