最近因爲疫情,大家都在家工作。爲了遠程連接,有些小的辦公室沒有使用虛擬專用網,而是直接在防火牆上進行了端口轉發,直接跳轉到服務器的3389端口上。而且由於各種原因,防火牆上也沒有限制source IP,這樣導致的結果就是互聯網上任何人都可以進行訪問。即使把外網端口改的特別大,但是對於掃描軟件而已,也就是時間的問題,並不能提升太多的安全。
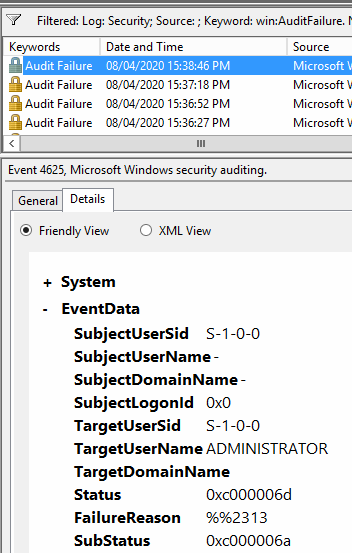
豆子今天就遇見了一起這樣的問題。某診所的服務器連續重啓,登進去一看,發現安全日誌裏面都是各種失敗的驗證事件。而且這個服務器也沒安裝任何安全軟件,完全在裸奔。
這樣看起來不方便,寫個簡單的腳本查詢一下
function get-hacker{
$eventcritea = @{logname='security';id=4625}
$Events =get-winevent -FilterHashtable $eventcritea -MaxEvents 1000
#$Events = Get-WinEvent -ComputerName syddc01 -FilterHashtable $eventcritea
# Parse out the event message data
ForEach ($Event in $Events) {
# Convert the event to XML
$eventXML = [xml]$Event.ToXml()
# Iterate through each one of the XML message properties
For ($i=0; $i -lt $eventXML.Event.EventData.Data.Count; $i++) {
# Append these as object properties
Add-Member -InputObject $Event -MemberType NoteProperty -Force -Name $eventXML.Event.EventData.Data[$i].name -Value $eventXML.Event.EventData.Data[$i].'#text'
}
}
$events | select TimeCreated, TargetUserName, ipAddress
}
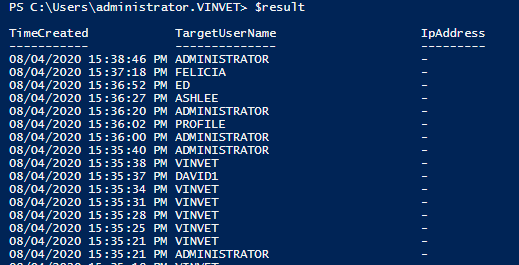
$result=get-hacker結果如下,可以看見對方嘗試了不同的用戶名,但是沒有顯示IP地址
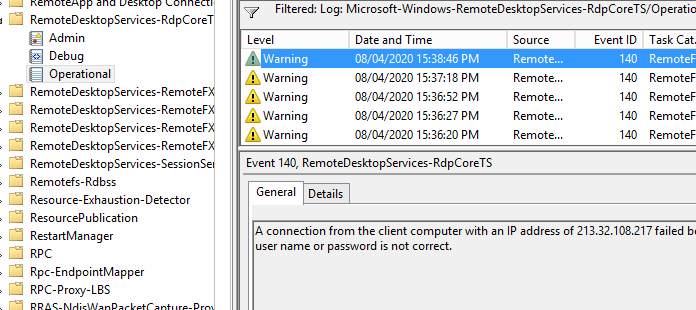
不用急,在對應的RemoteDesktopService-RdpCoreTS/Operation 日誌裏面,我們可以查看到真實的IP地址,如下所示,可以看見在看的同時,對方還在不斷地掃描,嘗試字典破解密碼
稍微修改一下上面的腳本,重新掃描一下
function get-hacker{
$eventcritea = @{logname='Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational';id=140}
$Events =get-winevent -FilterHashtable $eventcritea -MaxEvents 1000
#$Events = Get-WinEvent -ComputerName syddc01 -FilterHashtable $eventcritea
# Parse out the event message data
ForEach ($Event in $Events) {
# Convert the event to XML
$eventXML = [xml]$Event.ToXml()
# Append these as object properties
Add-Member -InputObject $Event -MemberType NoteProperty -Force -Name IP -Value $eventXML.Event.EventData.Data.'#text'
}
$events
}
$result=get-hacker
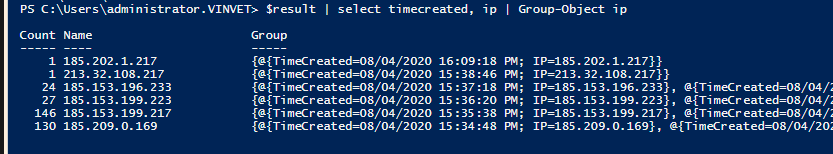
$result | select timecreated, IP | group-object ip
可以看見對方的惡意掃描來自於這6個地址
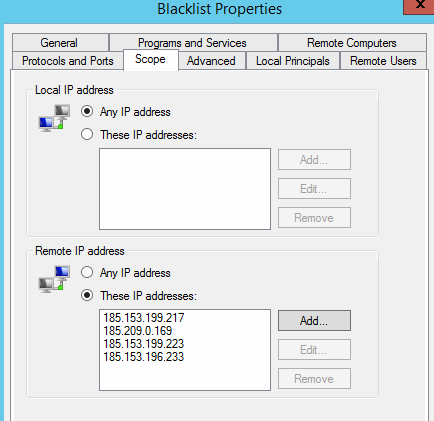
這個診所的路由器因爲過於垃圾,無法配置防火牆策略,於是我乾脆在Windows 的防火牆上新建了一條策略,對這幾個IP地址進行了Block。
之後再掃描日誌,沒有發現新的報錯信息,證明攔截有效。
然後在安裝殺軟,清理了一堆惡意文件出來。
過了一會,發現又有新的IP在掃描,於是稍微整理了一下腳本,讓他可以自動添加IP到防火牆rule裏面
function get-hacker{
Param
(
# Param1 help description
[Parameter(Mandatory=$true,
ValueFromPipelineByPropertyName=$true,
Position=0)]
[string]
$name,
# Param2 help description
[int]
$id
)
$eventcritea = @{logname=$name;id=$id}
$Events =get-winevent -FilterHashtable $eventcritea -MaxEvents 1000
#$Events = Get-WinEvent -ComputerName syddc01 -FilterHashtable $eventcritea
# Parse out the event message data
ForEach ($Event in $Events) {
# Convert the event to XML
$eventXML = [xml]$Event.ToXml()
# Iterate through each one of the XML message properties
#For ($i=0; $i -lt $eventXML.Event.EventData.Data.Count; $i++) {
# Append these as object properties
Add-Member -InputObject $Event -MemberType NoteProperty -Force -Name IP -Value $eventXML.Event.EventData.Data.'#text'
#}
}
$events
}
$result=get-hacker -name 'Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational' -id 140
$ip=$result | select timecreated, ip | Group-Object ip |select -ExpandProperty Name
function Add-MvaNetFirewallRemoteAdressFilter {
<#
.SYNOPSIS
This function adds one or more ipaddresses to the firewall remote address filter
.DESCRIPTION
With the default Set-NetFirewallAddressFilter you can set an address filter for a firewall rule. You can not use it to
add a ip address to an existing address filter. The existing address filter will be replaced by the new one.
The Add-MvaNetFirewallRemoteAdressFilter function will add the ip address. Which is very usefull when there are already
many ip addresses in de address filter.
.PARAMETER fwAddressFilter
This parameter conntains the AddressFilter that you want to change. It accepts pipeline output from the command
Get-NetFirewallAddressFilter
.PARAMETER IPaddresses
This parameter is mandatory and can contain one or more ip addresses. You can also use a subnet.
.EXAMPLE
Get-NetFirewallrule -DisplayName 'Test-Rule' | Get-NetFirewallAddressFilter | Add-MvaNetFirewallRemoteAdressFilter -IPAddresses 192.168.5.5
Add a single IP address to the remote address filter of the firewall rule 'Test-Rule'
.EXAMPLE
Get-NetFirewallrule -DisplayName 'Test-Rule' | Get-NetFirewallAddressFilter | Add-MvaNetFirewallRemoteAdressFilter -IPAddresses 192.168.5.5, 192.168.6.6, 192.168.7.0/24
Add multiple IP address to the remote address filter of the firewall rule 'Test-Rule'
.LINK
https://get-note.net/2018/12/31/edit-firewall-rule-scope-with-powershell/
.INPUTS
Microsoft.Management.Infrastructure.CimInstance#root/standardcimv2/MSFT_NetAddressFilter
.OUTPUTS
None
.NOTES
You need to be Administator to manage the firewall.
#>
[CmdletBinding()]
param(
[Parameter(ValueFromPipeline = $true,
Mandatory = $True)]
[psobject]$fwAddressFilter,
# Parameter help description
[Parameter(Position = 0,
Mandatory = $True,
HelpMessage = "Enter one or more IP Addresses.")]
[string[]]$IPAddresses
)
process {
try {
#Get the current list of remote addresses
[string[]]$remoteAddresses = $fwAddressFilter.RemoteAddress
Write-Verbose -Message "Current address filter contains: $remoteAddresses"
#Add new ip address to the current list
if ($remoteAddresses -in 'Any', 'LocalSubnet', 'LocalSubnet6', 'PlayToDevice') {
$remoteAddresses = $IPAddresses
}
else {
$remoteAddresses += $IPAddresses
}
#set new address filter
$fwAddressFilter | Set-NetFirewallAddressFilter -RemoteAddress $remoteAddresses -ErrorAction Stop
Write-Verbose -Message "New remote address filter is set to: $remoteAddresses"
}
catch {
$PSCmdlet.ThrowTerminatingError($PSitem)
}
}
}
$current=Get-NetFirewallRule -DisplayName 'blacklist' | Get-NetFirewallAddressFilter
$lists=$current | select -ExpandProperty RemoteAddress
foreach($i in $ip){
if ($lists -contains $i){
Write-Host "$i is already in the scope of blacklist" -ForegroundColor Green
}
else{
$current | Add-MvaNetFirewallRemoteAdressFilter -IPAddresses $i
}
}這樣一個臨時的繃帶療法就搞定了,稍後需要配置一個新的路由器去替代對方的老古董