Who is Softlayer
SoftLayer, an IBM Company, provides cloud infrastructure as a service from 13 data centers in the United States, Asia, and Europe, and a global footprint of 17 network points of presence. Our customers range from Web startups to global enterprises.
Products and services include bare metal and virtual servers, networking, turnkey big data and private cloud solutions, and more. Our unique advantages include the industry's first Network-Within-a-Network topology for true out-of-band access, and an easy-to-use customer portal and robust API for full remote-access of all product and service management options.
SoftLayer was founded in 2005 and is headquartered in Dallas, Texas. We were acquired by IBM in July, 2013.
Softlayer offer IPSec *** on private network for customer to connect their coporate network to Softlayer Cloud to manage their systems running on Softlayer Cloud.
Softlayer customer can complete Softlayer end's IPSec configuration through Softlayer customer portal.
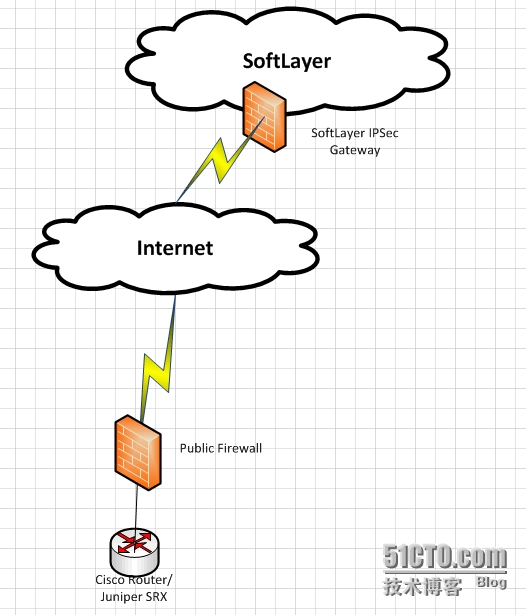
I will shows you the capacity of Softlayer IPSec in the series of articles by 3 user cases. The Network Topology is:
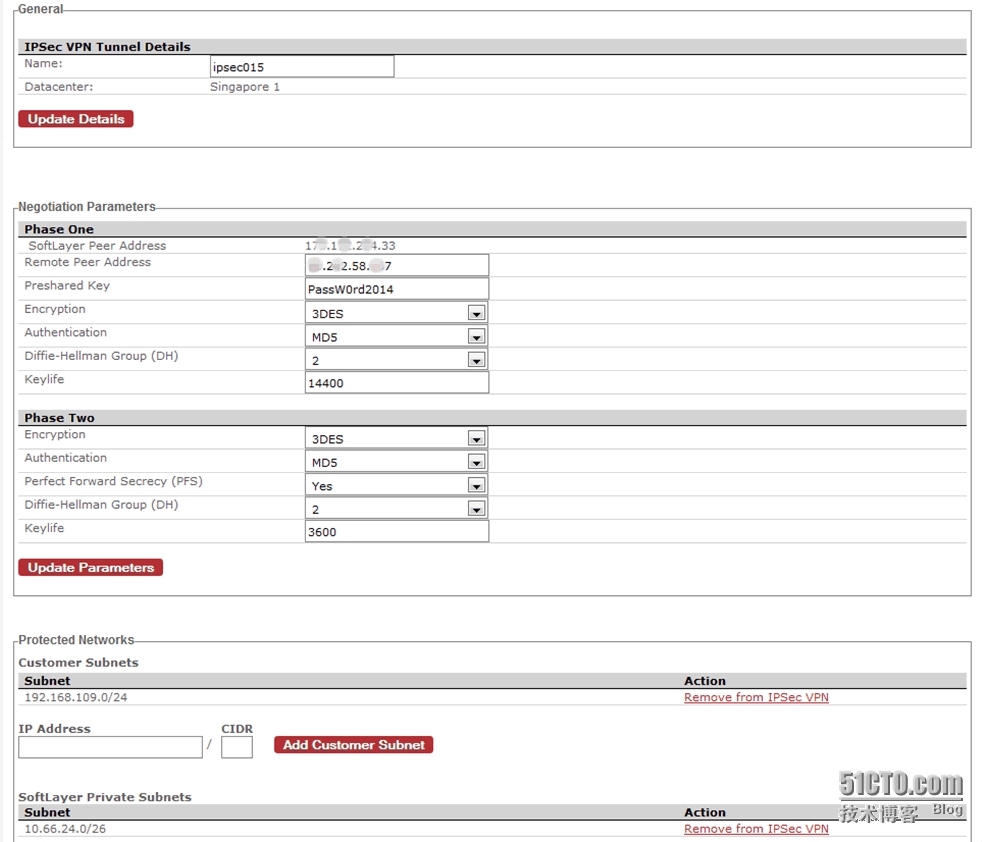
In the 3 user cases,we will use the same config on Softlayer end as below:
From the above, you can see the IPSec config on Softlayer end is quite straightforward: Phase 1 and Phase 2 nego parameters then customer subnets and Softlayer subnets.
Next-step is the configuration on customer end:
(1) Customer end is Cisco router.
Please note it looks like that Softlayer doesn't support the Cisco IPSec Virtual Tunnel interface.So you possibly have to use the classical "Crypto Map" method:
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
lifetime 14400
crypto isakmp key PassW0rd2014 address x.x.x.x (Softlayer end IPSec *** Gateway IP)
!
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
!
crypto map CMAP 10 ipsec-isakmp
set peer x.x.x.x
set transform-set TS
set pfs group2
match address ***
!
!
!
!
interface FastEthernet0/0
ip address 10.1.1.231 255.255.255.0
duplex auto
speed auto
crypto map CMAP
!
ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 10.1.1.1
!
!
!
!
ip access-list extended ***
permit ip 192.168.109.0 0.0.0.255 10.66.24.0 0.0.0.63
#192.168.109.0/24 customer end IP range
#10.66.24.0/26 Softlayer VM IP range
#This cisco router is behind a firewall which performs the NAT function