參考 [http://blog.csdn.net/lic95/article/details/48264933 CentOS6.X 配置L2TP For IPsec *服務器 詳細步驟]
基於阿里雲新加坡的centos6.x搭建l2tp+ipsec V\P\N**
1安裝幾個需要的軟件包
yum install wget lsof vim nss 2【我是阿里雲機器默認是阿里雲的源不用修改】改下yum源,使用阿里雲的yum源
https://me.jinchuang.org/archives/37.html centos|ubuntu更改yum源爲阿里雲的yum源
#安裝開發軟件包組
yum groupinstall "Development tools" -y3安裝ipsec 和 xl2tpd
#openswan 也就是ipsec
yum install openswan
#由於yum源中沒有,我們手動下載xl2tpd rpm包
wget http://dl.fedoraproject.org/pub/epel/6/x86_64/Packages/x/xl2tpd-1.3.8-1.el6.x86_64.rpm
#這裏安裝xl2tpd 會自動把ppp和其他需要的包給安裝上
yum install xl2tpd-1.3.8-1.el6.x86_64.rpm4配置ipsec預共享祕鑰,和修改配置文件
#添加預共享祕鑰
vim /etc/ipsec.secrets
include /etc/ipsec.d/*.secrets
#下面一行爲添加的: ip可以爲任意也可以爲你的外網ip地址,"***"就是連接時需要用的祕鑰,自己定義即可
0.0.0.0 %any: PSK "***"
#修改ipsec.conf 配置文件
vim /etc/ipsec.conf
config setup
protostack=netkey
dumpdir=/var/run/pluto/
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10
include /etc/ipsec.d/*.conf
#下面爲新添加,注意left這個IP地址,如果你是雲服務器且還只能看到內網ip看不到外網ip的,這裏就填寫內網ip地址。
conn l2tp-psk
rightsubnet=vhost:%priv
also=l2tp-psk-nonat
conn l2tp-psk-nonat
authby=secret
pfs=no
auto=add
keyingtries=3
rekey=no
ikelifetime=8h
keylife=1h
type=transport
left=172.18.212.34
leftprotoport=17/1701
right=%any
rightprotoport=17/%any
dpddelay=40
dpdtimeout=130
dpdaction=clear
sha2-truncbug=yes5修改xl2tpd 相關配置文件
#修改***連接ip 和 分配客戶端的地址池
vim /etc/xl2tpd/xl2tpd.conf
[global]
#連接ip地址,我用的彈性ip地址,機器內看不到外網ip這裏就填寫內網ip地址
listen-addr = 172.18.212.34
#分配的地址網段自定義即可
[lns default]
ip range = 192.168.1.128-192.168.1.254
local ip = 192.168.1.1
require chap = yes
refuse pap = yes
require authentication = yes
name = Linux***server
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes
#修改撥入獲取的dns
vim /etc/ppp/options.xl2tpd
ipcp-accept-local
ipcp-accept-remote
#dns根據實際情況情況而定,你上國際網站那就默認的即可,加速的話用國內dns即可
ms-dns 8.8.8.8
ms-dns 114.114.114.114
noccp
auth
crtscts
idle 1800
mtu 1410
mru 1410
nodefaultroute
debug
lock
proxyarp
connect-delay 50006配置連接的用戶賬號和密碼
vim /etc/ppp/chap-secrets
#按格式添加即可,中間用空格或者tab隔開
# Secrets for authentication using CHAP
# client server secret IP addresses
jinc * 123456 *7現在配置內核選項,linux的路由轉發等
vim /etc/sysctl.conf
#如果有的直接修改,沒有的添加
net.ipv4.ip_forward = 1 #修改爲1 表示打開路由轉發功能
net.ipv4.conf.all.rp_filter=0
net.ipv4.conf.all.accept_source_route=0
net.ipv4.conf.all.accept_redirects=0
net.ipv4.conf.all.send_redirects=0
net.ipv4.conf.default.rp_filter=0
net.ipv4.conf.default.accept_source_route=0
net.ipv4.conf.default.accept_redirects=0
net.ipv4.conf.default.send_redirects=0
net.ipv4.conf.eth0.accept_source_route=0
net.ipv4.conf.eth0.accept_redirects=0
net.ipv4.conf.eth0.send_redirects=0
net.ipv4.conf.eth0.rp_filter=0
net.ipv4.conf.lo.accept_source_route=0
net.ipv4.conf.lo.accept_redirects=0
net.ipv4.conf.lo.send_redirects=0
net.ipv4.conf.lo.rp_filter=0
#使修改的配置生效
sysctl -p
#啓動服務 這裏如果啓動失敗或者報錯,請檢查配置文件,或是否安裝了需要的包
service xl2tpd start
service ipsec start
#驗證ipsec 是否完全正確
ipsec verify
#一般來說 沒有error 和fail 就可以了,對應有問題的可能是少裝什麼包或者哪裏沒有配置好
Verifying installed system and configuration files
Version check and ipsec on-path [OK]
Libreswan 3.15 (netkey) on 2.6.32-696.10.1.el6.x86_64
Checking for IPsec support in kernel [OK]
NETKEY: Testing XFRM related proc values
ICMP default/send_redirects [OK]
ICMP default/accept_redirects [OK]
XFRM larval drop [OK]
Pluto ipsec.conf syntax [OK]
Hardware random device [N/A]
Checking rp_filter [OK]
Checking that pluto is running [OK]
Pluto listening for IKE on udp 500 [OK]
Pluto listening for IKE/NAT-T on udp 4500 [OK]
Pluto ipsec.secret syntax [OK]
Checking 'ip' command [OK]
Checking 'iptables' command [OK]
Checking 'prelink' command does not interfere with FIPSChecking for obsolete ipsec.conf options [OK]
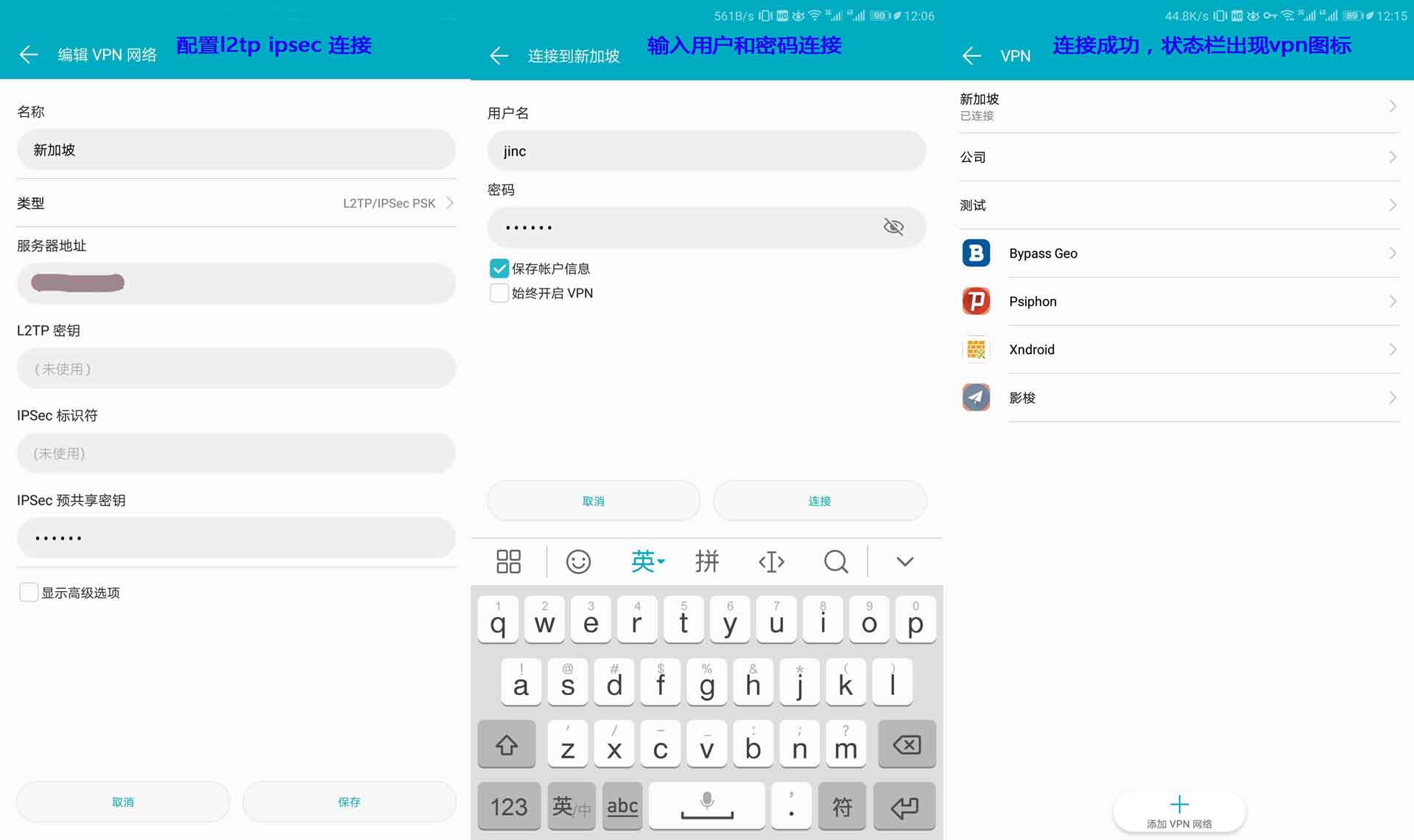
Opportunistic Encryption [DISABLED]8手機端配置連接
#觀察日誌
Mar 6 12:05:32 debug010000002015 xl2tpd[23389]: Connection established to 210.123.73.45, 58164. Local: 65126, Remote: 50489 (ref=0/0). LNS session is 'default'
Mar 6 12:05:32 debug010000002015 xl2tpd[23389]: Call established with 210.123.73.45, Local: 8094, Remote: 17899, Serial: -1408866546
Mar 6 12:05:32 debug010000002015 pppd[24590]: pppd 2.4.5 started by root, uid 0
Mar 6 12:05:32 debug010000002015 pppd[24590]: Using interface ppp0
Mar 6 12:05:32 debug010000002015 pppd[24590]: Connect: ppp0 <--> /dev/pts/1
Mar 6 12:05:32 debug010000002015 pppd[24590]: Unsupported protocol 'Compression Control Protocol' (0x80fd) received
Mar 6 12:05:32 debug010000002015 pppd[24590]: Cannot determine ethernet address for proxy ARP
Mar 6 12:05:32 debug010000002015 pppd[24590]: local IP address 192.168.1.1
Mar 6 12:05:32 debug010000002015 pppd[24590]: remote IP address 192.168.1.129
9如果以上的配置都沒有問題,連接也是沒問題的了,但是連接後不能上網的,接下來配置iptables轉發
#我這裏清空所有規則,只配置了轉發的方便測試。
iptables -F
iptables -F -t nat
iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -o eth0 -j MASQUERADE
iptables -I FORWARD -s 192.168.1.0/24 -j ACCEPT
iptables -I FORWARD -d 192.168.1.0/24 -j ACCEPT
service iptables save
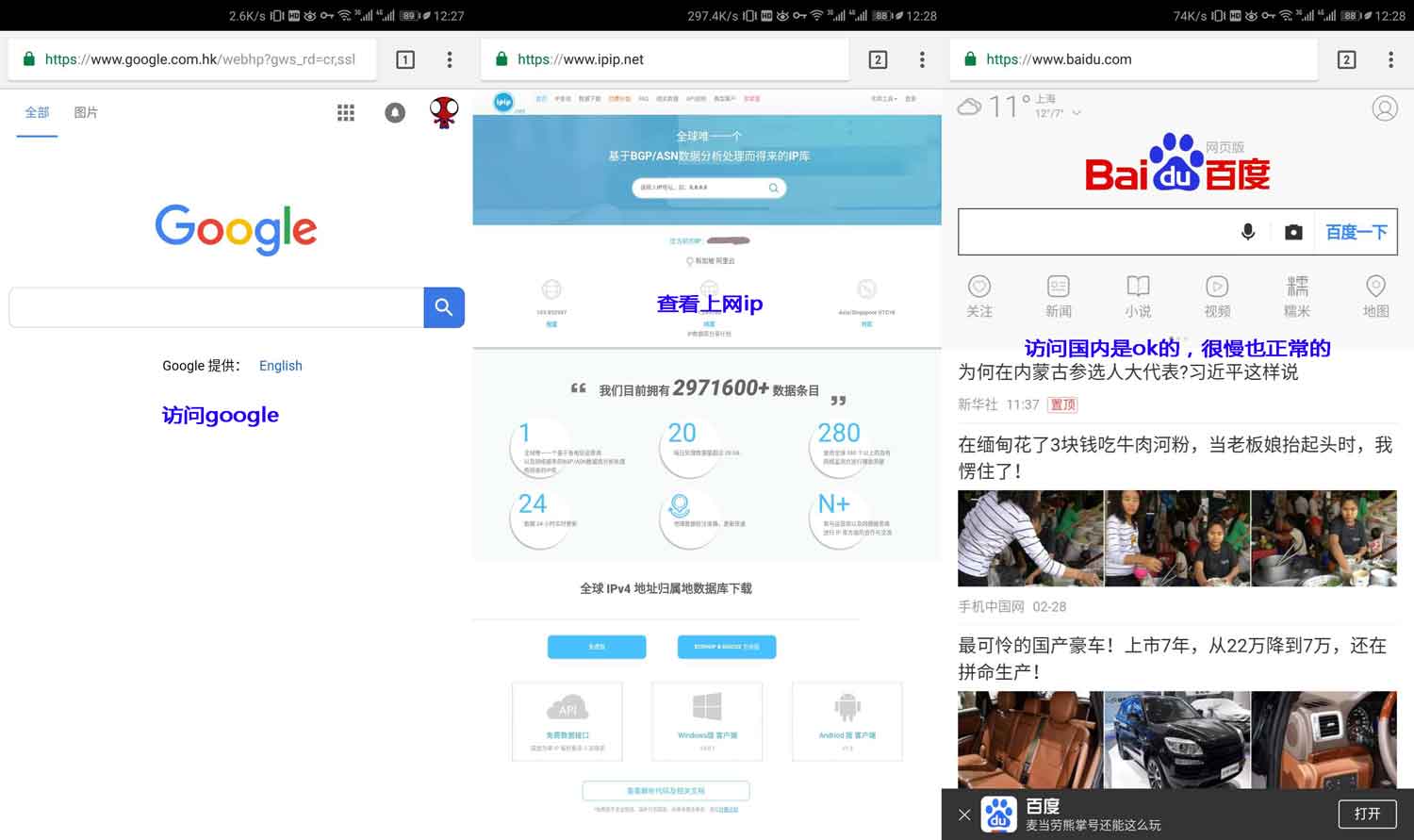
service iptables restart10手機訪問測試