IPSEC *** V1配置思路
IPsec ***安全策略配置流程圖
第一步:基本配置
FW1防火牆的配置
#
sysname FW1
#
interface GigabitEthernet0/0/0
ip address 202.1.1.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/0
ip address 192.168.1.254 255.255.255.0
service-manage ping permit
#
ip route-static 0.0.0.0 0.0.0.0 202.1.1.254
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet0/0/0
#
security-policy
default action permit
#FW2路由器的配置
#
sysname FW2
#
interface GigabitEthernet0/0/0
ip address 101.1.1.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/0
ip address 192.168.2.254 255.255.255.0
service-manage ping permit
#
ip route-static 0.0.0.0 0.0.0.0 101.1.1.254
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet0/0/0
#
security-policy
default action permit
#internet的配置
#
interface GigabitEthernet0/0/0
ip address 202.1.1.254 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 101.1.1.254 255.255.255.0
#檢查如下:
檢查FW1和PC1的通信
<FW1>ping 192.168.1.1
PING 192.168.1.1: 56 data bytes, press CTRL_C to break
Reply from 192.168.1.1: bytes=56 Sequence=1 ttl=128 time=40 ms
Reply from 192.168.1.1: bytes=56 Sequence=2 ttl=128 time=60 ms
Reply from 192.168.1.1: bytes=56 Sequence=3 ttl=128 time=40 ms
Reply from 192.168.1.1: bytes=56 Sequence=4 ttl=128 time=60 ms
Reply from 192.168.1.1: bytes=56 Sequence=5 ttl=128 time=50 ms
--- 192.168.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 40/50/60 ms檢查FW2和PC2的通信
[FW2]ping 192.168.2.2
PING 192.168.2.2: 56 data bytes, press CTRL_C to break
Reply from 192.168.2.2: bytes=56 Sequence=1 ttl=128 time=45 ms
Reply from 192.168.2.2: bytes=56 Sequence=2 ttl=128 time=53 ms
Reply from 192.168.2.2: bytes=56 Sequence=3 ttl=128 time=51 ms
Reply from 192.168.2.2: bytes=56 Sequence=4 ttl=128 time=52 ms
Reply from 192.168.2.2: bytes=56 Sequence=5 ttl=128 time=32 ms
--- 192.168.2.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 32/46/53 ms檢查FW1和FW2的通信
<FW1>ping 101.1.1.1
PING 101.1.1.1: 56 data bytes, press CTRL_C to break
Reply from 101.1.1.1: bytes=56 Sequence=1 ttl=254 time=30 ms
Reply from 101.1.1.1: bytes=56 Sequence=2 ttl=254 time=20 ms
Reply from 101.1.1.1: bytes=56 Sequence=3 ttl=254 time=40 ms
Reply from 101.1.1.1: bytes=56 Sequence=4 ttl=254 time=20 ms
Reply from 101.1.1.1: bytes=56 Sequence=5 ttl=254 time=30 ms
--- 101.1.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/28/40 ms檢查PC1和PC2的通信
PC>ping 192.168.2.2
Ping 192.168.2.2: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
Request timeout!
Request timeout!
Request timeout!
--- 192.168.2.2 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss第二步:IPSEC 階段一配置
IKE安全提議
在FW1和FW2分別配置如下
ike proposal 10 注意:安全提議是有默認配置,可以修改
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256 IKEv1中不用這個參數 IKEv2中使用這個參數
prf hmac-sha2-256
#檢查:
[FW1]display ike proposal
2020-03-14 14:25:22.420
Number of IKE Proposals: 2
-------------------------------------------
IKE Proposal: 10
Authentication Method : PRE_SHARED
Authentication Algorithm : SHA2-256
Encryption Algorithm : AES-256
Diffie-Hellman Group : MODP-2048
SA Duration(Seconds) : 86400
Integrity Algorithm : HMAC-SHA2-256
Prf Algorithm : HMAC-SHA2-256
-------------------------------------------配置IKE對等體(PEER)
FW1配置
ike peer fw2 -----------取名
pre-shared-key Huawei@123---------------如果採用預共享方式,配置密鑰
ike-proposal 10 -----------------------------調用安全提議
undo version 2-------------------------------關閉V2版本,默認就是V2版本
remote-address 101.1.1.1 -----------------如果是主模式必須配置對端的地址(固定地址)FW2配置
ike peer fw1
pre-shared-key Huawei@123
ike-proposal 10
undo version 2
remote-address 202.1.1.1檢查如下:
[FW1]display ike peer brief
2020-03-14 14:31:19.910
Current ike peer number: 1
---------------------------------------------------------------------------
Peer name Version Exchange-mode Proposal Id-type RemoteAddr
---------------------------------------------------------------------------
fw2 v1 main 10 IP 101.1.1.1第三步:IPSEC階段二配置
配置感興趣流(就是實際通信點)
FW1:
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
FW2
acl number 3000
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 注意:IKEV1感興趣流要互爲鏡像,必須是相互匹配的,不是包含或者不一樣的,都不能協商成功
IPSEC安全提議
在FW1和FW2配置
ipsec proposal 10
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256檢查:
[FW1]display ipsec proposal
2020-03-14 14:33:58.850
Number of proposals: 1
IPSec proposal name: 10
Encapsulation mode: Tunnel
Transform : esp-new
ESP protocol : Authentication SHA2-HMAC-256
Encryption AES-256
[FW1]配置IPSEC安全策略
FW1
ipsec policy ipsec_policy 10 isakmp
security acl 3000 -----------------------調用感興趣流
ike-peer fw2 ---------------------------調用IKE PEER
alias ipsec_policy_10
proposal 10 ---------------------------調用IPSEC安全
FW2
ipsec policy ipsec_policy 10 isakmp 後面接isakmp的話是自動方式
security acl 3000 -----------------------調用感興趣流
ike-peer fw1 ---------------------------調用IKE PEER
alias ipsec_policy_10
proposal 10 ---------------------------調用IPSEC安全物理接口調用
在FW1和FW2上配置
interface GigabitEthernet0/0/0
ipsec policy ipsec_policy 放行安全策略
FW1的配置
#
security-policy
rule name ipsec1
source-zone local
destination-zone untrust
source-address 202.1.1.0 mask 255.255.255.0
destination-address 101.1.1.0 mask 255.255.255.0
action permit
rule name ipsec2
source-zone untrust
destination-zone local
source-address 101.1.1.0 mask 255.255.255.0
destination-address 202.1.1.0 mask 255.255.255.0
action permit
rule name ipsec3
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
destination-address 192.168.2.0 mask 255.255.255.0
action permit
rule name ipsec4
source-zone untrust
destination-zone trust
source-address 192.168.2.0 mask 255.255.255.0
destination-address 192.168.1.0 mask 255.255.255.0
action permit
#FW2的配置
#
security-policy
rule name ipsec1
source-zone local
destination-zone untrust
source-address 101.1.1.0 mask 255.255.255.0
destination-address 202.1.1.0 mask 255.255.255.0
action permit
rule name ipsec2
source-zone untrust
destination-zone local
source-address 202.1.1.0 mask 255.255.255.0
destination-address 101.1.1.0 mask 255.255.255.0
action permit
rule name ipsec3
source-zone trust
destination-zone untrust
source-address 192.168.2.0 mask 255.255.255.0
destination-address 192.168.1.0 mask 255.255.255.0
action permit
rule name ipsec4
source-zone untrust
destination-zone trust
source-address 192.168.1.0 mask 255.255.255.0
destination-address 192.168.2.0 mask 255.255.255.0
action permit
#測試如下
默認如果沒有配置 auto-neg ,需要手動觸發(觸發感興趣流)
[FW1]display ike sa 檢查IKE SA,階段一的問題
2020-03-14 14:46:10.170
IKE SA information :
Conn-ID Peer *** Flag(s) Phase RemoteType RemoteID
------------------------------------------------------------------------------------------------------------------------------------
2 101.1.1.1:500 RD|ST|A v1:2 IP 101.1.1.1
1 101.1.1.1:500 RD|ST|A v1:1 IP 101.1.1.1
Number of IKE SA : 2
--------------------------------------------------------------------------------------------
Flag Description:
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP
M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING
對IKE SA參數的講解
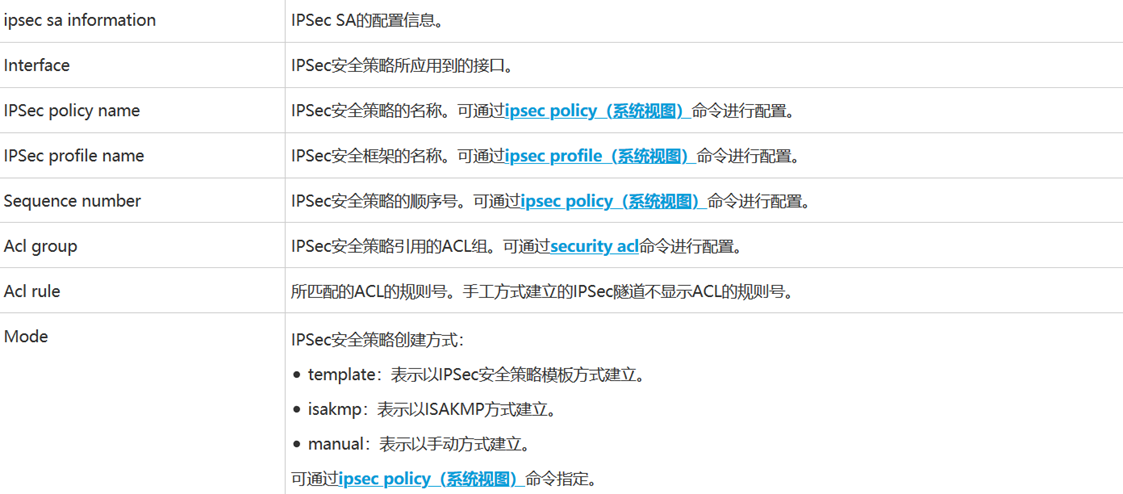
檢查ipsec sa
[FW1]display ipsec sa 檢查IPSEC SA ,階段二的問題
2020-03-14 14:48:03.850
ipsec sa information:
===============================
Interface: GigabitEthernet0/0/0
===============================
-----------------------------
IPSec policy name: "ipsec_policy"
Sequence number : 10
Acl group : 3000
Acl rule : 5
Mode : ISAKMP
-----------------------------
Connection ID : 2
Encapsulation mode: Tunnel
Holding time : 0d 0h 4m 38s
Tunnel local : 202.1.1.1:500
Tunnel remote : 101.1.1.1:500
Flow source : 192.168.1.0/255.255.255.0 0/0-65535
Flow destination : 192.168.2.0/255.255.255.0 0/0-65535
[Outbound ESP SAs]
SPI: 195032177 (0xb9ff471)
Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128
SA remaining key duration (kilobytes/sec): 10485760/3323
Max sent sequence-number: 5
UDP encapsulation used for NAT traversal: N
SA encrypted packets (number/bytes): 4/240
[Inbound ESP SAs]
SPI: 200897249 (0xbf972e1)
Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128
SA remaining key duration (kilobytes/sec): 10485760/3323
Max received sequence-number: 1
UDP encapsulation used for NAT traversal: N
SA decrypted packets (number/bytes): 4/240
Anti-replay : Enable
Anti-replay window size: 1024
[FW1]
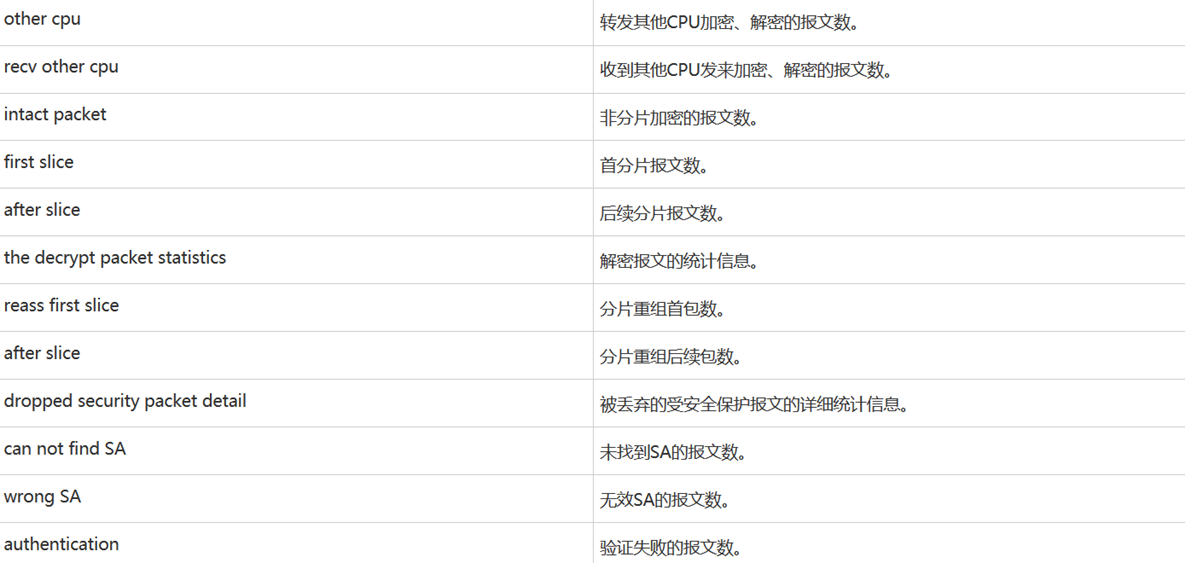
查看是否有加解密
[FW1]display ipsec statistics
2020-03-14 14:49:01.940
IPSec statistics information:
Number of IPSec tunnels: 1
Number of standby IPSec tunnels: 0
the security packet statistics:
input/output security packets: 5/4
input/output security bytes: 240/240
input/output dropped security packets: 1/0
the encrypt packet statistics: ------------------加密
send chip: 4, recv chip: 4, send err: 0
local cpu: 4, other cpu: 0, recv other cpu: 0
intact packet: 4, first slice: 0, after slice: 0
the decrypt packet statistics:
send chip: 5, recv chip: 4, send err: 1------------------解密
local cpu: 4, other cpu: 0, recv other cpu: 0
reass first slice: 0, after slice: 0
dropped security packet detail:
can not find SA: 0, wrong SA: 0
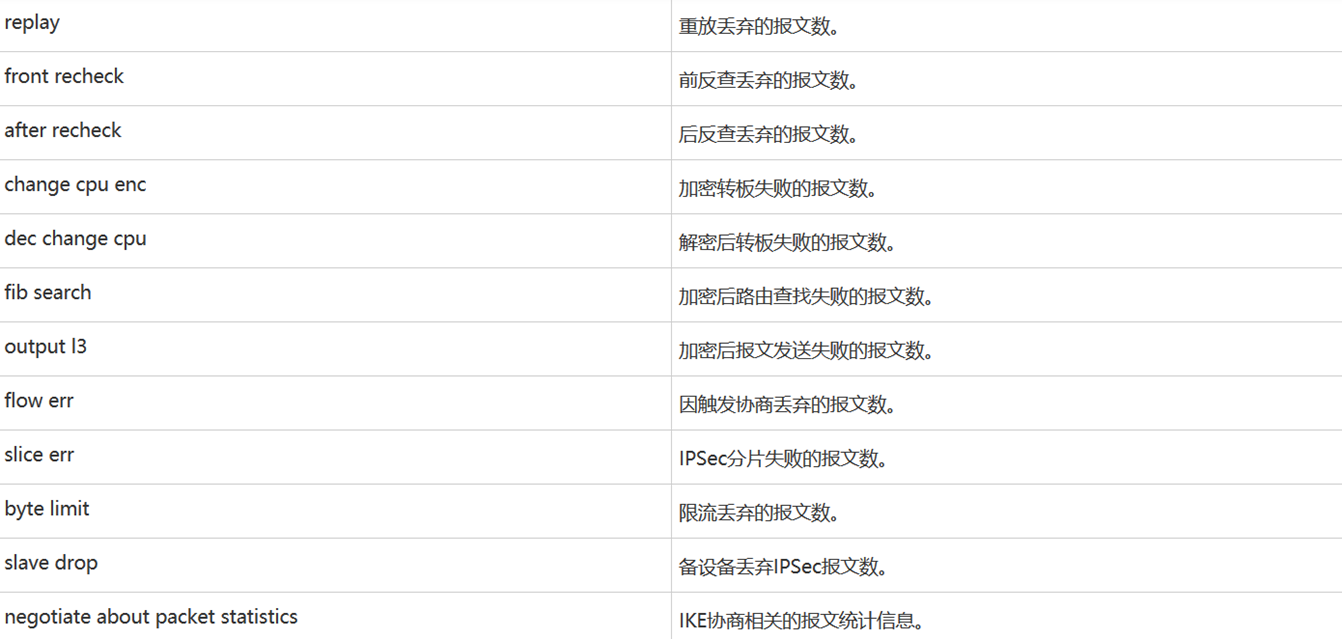
authentication: 1, replay: 0
front recheck: 0, after recheck: 0
change cpu enc: 0, dec change cpu: 0
fib search: 0, output l3: 0
flow err: 0, slice err: 0, byte limit: 0
slave drop: 0
negotiate about packet statistics:
IKE fwd packet ok: 4, err: 0
IKE ctrl packet inbound ok: 4, outbound ok: 5
SoftExpr: 0, HardExpr: 0, DPDOper: 0
trigger ok: 1, switch sa: 1, sync sa: 0
recv IKE nat keepalive: 0, IKE input: 0
[SZ_***]display ipsec statistics
11:56:09 2019/08/04
the security packet statistics:
input/output security packets: 7/7
input/output security bytes: 420/420
input/output dropped security packets: 0/0
the encrypt packet statistics
send sae:7, recv sae:7, send err:0
local cpu:7, other cpu:0, recv other cpu:0
intact packet:5, first slice:0, after slice:0
the decrypt packet statistics
send sae:7, recv sae:7, send err:0
local cpu:0, other cpu:0, recv other cpu:0
reass first slice:0, after slice:0, len err:0
dropped security packet detail:
no enough memory: 0, too long: 0
can't find SA: 0, wrong SA: 0
authentication: 0, replay: 0
front recheck: 0, after recheck: 0
exceed byte limit: 0, exceed packet limit: 0
change cpu enc: 0, dec change cpu: 0
change datachan: 0, fib search: 0
rcv enc(dec) form sae said err: 0, 0
port number error: 0
send port: 0, output l3: 0, l2tp input: 0
negotiate about packet statistics:
IP packet ok:1, err:0, drop:0
IP rcv other cpu to ike:0, drop:0
IKE packet inbound ok:4, err:0
IKE packet outbound ok:11, err:0
SoftExpr:0, HardExpr:0, DPDOper:0, SwapSa:0
ModpCnt: 2, SaeSucc: 2, SoftwareSucc: 0
[FW1] 注:必須要加解密,才能代表IPSEC成功