前言:
-
SSH遠程管理
1.配置OpenSSH服務端
2.使用SSH客戶端程序
3.密鑰對驗證的SSH體系
-
TCP Wrappers概述 (針對程序的管理機制)
1.TCP Wrappers 概述
2.TCP Wrappers訪問策略
一 :openSSH服務器遠程訪問
1.1 ssh協議
- 爲客戶機提供安全的shell環境,用於遠程管理
- 默認端口:TCP 22
1.2 openssh
- 服務名稱 :sshd
- 服務端主程序: /usr/sbin/sshd
- 服務端配置文件: /etc/ssh/sshd_config
第二種遠程訪問:telnet 也是遠程訪問,是不會經過加密的明文傳輸,可以用抓包工具直接獲取其中的消息 23 tcp 端口;而ssh 是典型的密文訪問
因此tlelent 主要應用於局域網;ssh皆可
第三種遠程訪問是遠程桌面,3389端口號,帶有圖形化訪問
例:mstsc命令 windows 中的遠程桌面訪問形式
通過遠程訪問的用戶必須給其設置密碼
vnc軟件可以跨微軟系統和linux系統之間連接
teamviewer軟件 手機連接電腦
被遠程方可以手動關閉拒絕遠程
ssh_config 是針對客戶端的
shhd_config是服務端
1.2 服務監聽選項
- 端口號、協議版本、監聽IP地址
- 禁用反向解析
[root@localhost ~]# vim /etc/ssh/sshd_config
......
#Port 22 '端口號(可以修改)'
#ListenAddress 0.0.0.0 '監聽地址'
Protocol 2 '版本'
#UseDNS no 'DNS反向解析 否'
控制
- 禁止ROOt用戶、空密碼用戶 ————用戶層面的控制
- 登錄時間、重試次數 ————用戶屬性的控制
- AllowUsers、DenyUsers ————使用白黑名單控制
AllowUsers 白名單 :僅允許登陸
DenyUsers 黑名單 :僅拒絕登陸
[root@localhost ~]# vim /etc/ssh/sshd_config
#LoginGraceTime 2m '登錄時間2min 超過2min自動註銷'
#PermitRootLogin yes '允許root登陸 是 前面有#符號註釋則不可以使用'
#StrictModes yes '嚴格遵循標準模式 是'
#MaxAuthTries 6 '最大嘗試登陸次數爲 6'
#MaxSessions 10 '最大創建會話爲 10'
PermitEmptPasswords no '允許空密碼登陸 否'
······
AllowUsers jerry [email protected]
'白名單,只允許以下用從指定終端登錄,用戶與用戶之間用空格隔開'AllowUsers的權限比DenyUsers的權限大,AllowsUsers不要與DenyUsers同時用
1.3 登陸驗證
1.3.1 登陸驗證對象
- 服務器中的本地用戶賬號
1.3.2 登陸驗證方式
- 密碼驗證: 覈對用戶名、密碼是否匹配
- 密鑰對驗證: 覈對客戶的私鑰、服務端公鑰是否匹配
密鑰對的方式需要自己去創建
密鑰對裏面包含公鑰和私鑰,合在一起叫密鑰對
公鑰給對方,私鑰自己保留,這種方式叫做非對稱密鑰 rsa 相當於虎符
des 或aex或3des模式 是對稱密鑰,相當於門鑰匙
[root@localhost ~]# vim /etc/ssh/sshd_config
······
#PubkeyAuthentication yes '密鑰對驗證開啓 是'
#PasswordAuthentication yes '身份密碼驗證 是'
AuthorizedKeysFile .ssh/authorized_keys '密鑰對公鑰庫文件路徑'啓用密碼密碼驗證、密鑰對驗證、指定公鑰庫位置
二 : 使用SSH客戶端程序
2.1 ssh命令 ————遠程安全登錄
ssh user@host
ssh 被連接的主機的本地用戶名@主機名
選項 -p 即 指定端口號
2.2 scp命令 ———— 遠程安全複製
scp user@host:file 1 file2
複製目標主機下面的file文件到自己的file2下
scp file1 user@host:file2
複製自己的file1下的文件到目標主機的file1下
2.3 sftp命令 ————安全FTP上下載
sftp user@host
進入到目標主機的sftp模式
2.4.1 ssh命令 遠程安全登錄
test01 的ip地址爲192.168.139.128
test02的ip地址爲192.168.139.129
[root@test01 ~]# cd /etc/ssh '切換到/etc/ssh目錄下'
[root@test01 ssh]# ls
moduli ssh_host_ecdsa_key ssh_host_ed25519_key.pub
ssh_config ssh_host_ecdsa_key.pub ssh_host_rsa_key
sshd_config ssh_host_ed25519_key ssh_host_rsa_key.pub
[root@test01 ssh]# vim sshd_config '編輯服務端配置文件'
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
16 #
17 Port 22 '端口號22,去掉#啓用'
18 #AddressFamily any
19 #ListenAddress 0.0.0.0
20 #ListenAddress ::
21
22 HostKey /etc/ssh/ssh_host_rsa_key
23 #HostKey /etc/ssh/ssh_host_dsa_key
24 HostKey /etc/ssh/ssh_host_ecdsa_key
25 HostKey /etc/ssh/ssh_host_ed25519_key
26
[root@test01 ssh]# systemctl restart sshd '重啓sshd服務'
[root@test02 ~]# ssh [email protected] '連接開啓遠程服務的主機,以root身份登陸'
The authenticity of host '192.168.139.128 (192.168.139.128)' can't be established.
ECDSA'指密鑰對' key fingerprint is SHA256:dXWxtS2ShXQgfb7R672V7+l3i7rGqHBbIB5MTcFnAws.
ECDSA'指密鑰對' key fingerprint is MD5:59:fb:20:f0:28:96:5e:14:90:82:63:c9:ae:67:d6:e9.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.139.128' (ECDSA) to the list of known hosts.
[email protected]'s password:
Last login: Wed Nov 20 17:13:57 2019
[root@test01 ~]# '注意主機名,此時已經遠程登陸成功'
[root@test01 ~]# ifconfig '查看自身的i網卡(此時已經遠程到test01上)'
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.139.128 netmask 255.255.255.0 broadcast 192.168.139.255
[root@test01 ~]# exit '退出'
logout
Connection to 192.168.139.128 closed.
[root@test02 ~]# ifconfig '查看自身的主機名,test02的主機名'
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.139.129 netmask 255.255.255.0 broadcast 192.168.139.255
[root@test02 ~]# ssh [email protected] ''用gsy的身份去登陸,也可以
[email protected]'s password:
Last login: Wed Nov 20 18:07:37 2019
[gsy@test01 ~]$ exit '退出'
logout
Connection to 192.168.139.128 closed.遠程連接目標主機時,使用root或普通用戶都可以
[root@test01 ssh]# vim /etc/ssh/sshd_config '配置28的sshd的服務端配置文件'
38 PermitRootLogin no '第38行取消註釋符,root登陸否'
[root@test01 ssh]# systemctl restart sshd '重啓ssh服務以生效配置'[root@test02 ~]# ssh [email protected] '去連28,使用root身份,'
The authenticity of host '192.168.139.128 (192.168.139.128)' can't be established.
ECDSA key fingerprint is SHA256:dXWxtS2ShXQgfb7R672V7+l3i7rGqHBbIB5MTcFnAws.
ECDSA key fingerprint is MD5:59:fb:20:f0:28:96:5e:14:90:82:63:c9:ae:67:d6:e9.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.139.128' (ECDSA) to the list of known hosts.
[email protected]'s password:
Permission denied, please try again. '拒絕權限,請重試'
[email protected]'s password:
[root@test02 ~]#
[root@test02 ~]# ssh [email protected] '使用gsy身份去連接,沒問題'
[email protected]'s password:
Last login: Wed Nov 20 18:08:14 2019 from 192.168.139.129
[gsy@test01 ~]$
[gsy@test01 ~]$ su - root '然後su切換到root'
Password:
Last login: Wed Nov 20 18:30:29 CST 2019 on pts/5
Last failed login: Wed Nov 20 18:32:37 CST 2019 on pts/5
There was 1 failed login attempt since the last successful login.
[root@test01 ~]# '成功'
permission denied 權限拒絕
爲了不讓普通用戶與root之間隨意切換,可以在服務端28 配置pam.d/su,啓用pam.d/su後,不在wheel組內的用戶無法
[root@test01 ssh]# vim /etc/pam.d/su '編輯對應的配置文件'
6 auth required pam_wheel.so use_uid '取消註釋,啓用pam.d的su功能'
[root@test01 ssh]# useradd lisi '新創建用戶lisi,該用戶不在wheel組內'
[root@test01 ssh]# passwd lisi
Changing password for user lisi.
New password:
BAD PASSWORD: The password is shorter than 8 characters
Retype new password:
passwd: all authentication tokens updated successfully.[root@test02 ~]# ssh [email protected] '用29去鏈接28'
[email protected]'s password:
[lisi@test02 ~]$ 'lisi登陸成功'
[lisi@test02 ~]$ su - root 'su 切換root'
密碼:
su: 拒絕權限 '失敗'[root@test01 ssh]# vim /etc/ssh/sshd_config '給28配置sshd_config'
21 AllowUsers gsy '手動添加白名單,即只允許gsy登陸'
[root@test01 ssh]# systemctl restart sshd '重啓sshd服務'
[root@test02 ~]# ssh [email protected] '以gsy身份,29遠程28'
[email protected]'s password:
Last failed login: Wed Nov 20 18:51:43 CST 2019 from 192.168.139.129 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Wed Nov 20 18:48:54 2019 from 192.168.139.128
[gsy@test01 ~]$ logout '登陸成功,然後退出'
Connection to 192.168.139.128 closed.
[root@test02 ~]# ssh [email protected] '以root身份29去遠程28'
[email protected]'s password: '輸入密碼'
Permission denied, please try again. '權限拒絕,請重試'
[email protected]'s password:
Permission denied, please try again.
2.4.2 scp 命令——遠程安全複製
[root@test01 ssh]# vim /etc/hosts '此時在28,以hosts文件爲實驗'
test01 192.168.139.128 '增加內容'
test02 192.168.139.129 '增加內容'
[root@test01 ssh]# vim /etc/ssh/sshd_config '去配置sshd'
#AllowUsers gsy '取消白名單,即所有人都可登錄'
PermitRootLogin no '註釋掉遠程root登陸 否'
[root@test01 ssh]# systemctl restart sshd '重啓sshd服務'
[root@test02 ~]# ssh [email protected] '以root身份29去遠程28'
[email protected]'s password:
Last failed login: Wed Nov 20 19:05:55 CST 2019 from 192.168.139.129 on ssh:notty
There were 8 failed login attempts since the last successful login.
Last login: Wed Nov 20 18:41:42 2019 '登陸成功'
[root@test01 ssh]# scp /etc/hosts [email protected]:etc/hosts
'此時在28上,scp複製 本地 /etc/hosts文件 到29:/etc/hosts'
The authenticity of host '192.168.139.129 (192.168.139.129)' can't be established.
ECDSA key fingerprint is SHA256:+uy+1TNy69jB97B7+AoYqhNEaBi42DuOYb0oE4pJ8s0.
ECDSA key fingerprint is MD5:00:78:0c:c1:c2:7b:01:45:7c:31:c2:3b:53:4d:5c:10.
Are you sure you want to continue connecting (yes/no)? yes '詢問是否連接,選擇是'
Warning: Permanently added '192.168.139.129' (ECDSA) to the list of known hosts.
[email protected]'s password:
hosts 100% 204 87.9KB/s 00:00 '顯示進度'
[root@test01 ssh]#
[root@test01 ssh]# ssh [email protected] '以root身份28遠程29'
[email protected]'s password:
Last login: Wed Nov 20 19:18:41 2019 from 192.168.139.129
[root@test02 ~]# cat /etc/hosts '查看29下的/etc/hosts文件'
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
test01 192.168.139.128
test02 192.168.139.129
[root@test02 ~]# logout '註銷登陸'
Connection to 192.168.139.129 closed.
[root@test01 ssh]# cd /opt/
[root@test01 opt]# ls
rh
[root@test01 opt]# touch abc.txt '在本地創建空文件'
[root@test01 opt]# scp /opt/abc.txt [email protected]:/home/
'把本地的/opt/abc.txt文件 以root身份 複製到192.168.139.129主機的/home/目錄下'
[email protected]'s password: '密碼確認'
abc.txt 100% 0 0.0KB/s 00:00
[root@test01 opt]#
[root@test02 ~]# cd /home
[root@test02 home]# ls
abc.txt gsy
[root@test02 home]# vim /etc/ssh/sshd_config '修改sshd_config服務端配置'
Port 22 '開啓接口'
[root@test02 home]# systemctl restart sshd '重啓'
[root@test02 home]# mkdir abc
[root@test01 opt]# scp /opt/abc.txt [email protected]:/home/abc/
[email protected]'s password:
scp: /home/abc//abc.txt: Permission denied '複製失敗'
[root@test02 home]# ls -al
total 0
drwxr-xr-x. 4 root root 43 Nov 20 19:32 .
dr-xr-xr-x. 17 root root 224 Oct 24 15:42 ..
'drwxr-xr-x. 2 root root 6 Nov 20 19:32 abc '權限不夠'
-rw-r--r--. 1 root root 0 Nov 20 19:22 abc.txt
drwx------. 3 gsy gsy 78 Oct 24 15:36 gsy
[root@test02 home]# chmod 777 abc
[root@test02 home]# ls -al
total 0
drwxr-xr-x. 4 root root 43 Nov 20 19:32 .
dr-xr-xr-x. 17 root root 224 Oct 24 15:42 ..
'drwxrwxrwx. 2 root root 6 Nov 20 19:32 abc
-rw-r--r--. 1 root root 0 Nov 20 19:22 abc.txt
drwx------. 3 gsy gsy 78 Oct 24 15:36 gsy
[root@test02 home]#
[root@test01 opt]# scp /opt/abc.txt [email protected]:/home/abc/
'重試'
[email protected]'s password: '可以了'
abc.txt 100% 0 0.0KB/s 00:00 然後到29主機上查看驗證
[root@test02 home]# ls -al abc
total 0
drwxrwxrwx. 2 root root 21 Nov 20 19:38 .
drwxr-xr-x. 4 root root 43 Nov 20 19:32 ..
'-rw-r--r--. 1 gsy gsy 0 Nov 20 19:38 abc.txt
以什麼用戶傳過去的,就會以該用戶的屬主寫入
[root@test01 opt]# scp [email protected]:/home/gsy.txt /opt
'在28上,從29主機上以root身份去複製/home/gsy.txt文件 到/opt下'
[email protected]'s password:
gsy.txt '成功' 100% 4 1.4KB/s 00:00
[root@test01 opt]# ls -l
total 4
-rw-r--r--. 1 root root 0 Nov 20 19:21 abc.txt
'-rw-r--r--. 1 root root 4 Nov 20 19:46 gsy.txt'
drwxr-xr-x. 2 root root 6 Mar 26 2015 rh
[root@test01 opt]# cat gsy.txt
gsy
[root@test01 opt]#
想要ssh遠程其他,就需要吧其他的的權限放開
2.4.3 sftp命令 ————安全FTP上下載
[root@test01 ~]# sftp [email protected] 'ftp上下載方式連接29'
[email protected]'s password:
Connected to 192.168.139.129.
sftp>
sftp> ls -a
. .. .ICEauthority
.Xauthority .bash_history .bash_logout
.bash_profile .bashrc .cache
.config .cshrc .dbus
.esd_auth .local .mozilla
.ssh .tcshrc .viminfo
anaconda-ks.cfg initial-setup-ks.cfg 下載
公共 圖片 文檔
桌面 模板 視頻
音樂
sftp> cd /opt
sftp> ls
rh
sftp> mkdir aaa
sftp> ls
aaa rh
sftp> rm -rf aaa
rm: Invalid flag -r
sftp>
ls
aaa rh
sftp>
sftp> help
Available commands:
bye Quit sftp
cd path Change remote directory to 'path'
chgrp grp path Change group of file 'path' to 'grp'
chmod mode path Change permissions of file 'path' to 'mode'
chown own path Change owner of file 'path' to 'own'
df [-hi] [path] Display statistics for current directory or
filesystem containing 'path'
exit Quit sftp
get [-afPpRr] remote [local] Download file
reget [-fPpRr] remote [local] Resume download file
reput [-fPpRr] [local] remote Resume upload file
help Display this help text
lcd path Change local directory to 'path'
lls [ls-options [path]] Display local directory listing
lmkdir path Create local directory
ln [-s] oldpath newpath Link remote file (-s for symlink)
lpwd Print local working directory
ls [-1afhlnrSt] [path] Display remote directory listing
lumask umask Set local umask to 'umask'
mkdir path Create remote directory
progress Toggle display of progress meter
put [-afPpRr] local [remote] Upload file
pwd Display remote working directory
quit Quit sftp
rename oldpath newpath Rename remote file
rm path Delete remote file
rmdir path Remove remote directory
symlink oldpath newpath Symlink remote file
version Show SFTP version
!command Execute 'command' in local shell
! Escape to local shell
? Synonym for help
sftp> rmdir aaa
sftp> ls
rh
sftp>
在sftp模式下,命令跟linux的命令有些不一樣
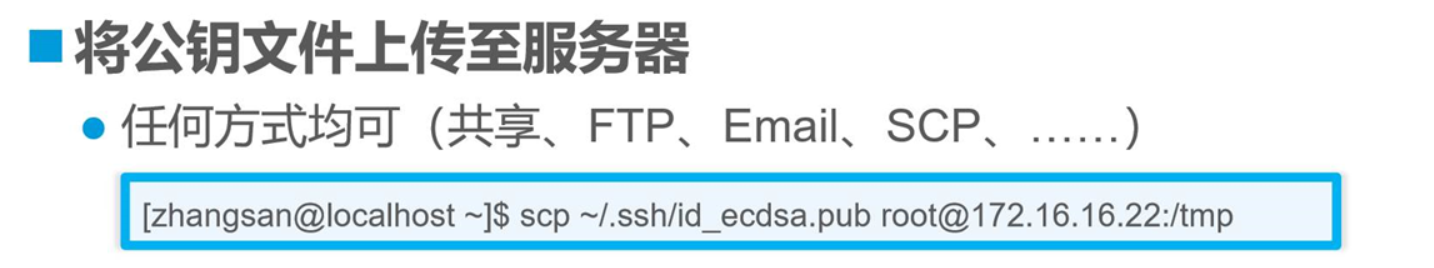
三 : 構建密鑰對驗證的SSH體系
[root@test02 ~]# ssh-keygen rsa ‘創建密鑰對的選項’
Too many arguments.
usage: ssh-keygen [-q] [-b bits] [-t dsa | ecdsa | ed25519 | rsa | rsa1]
[-N new_passphrase] [-C comment] [-f output_keyfile]
ssh-keygen -p [-P old_passphrase] [-N new_passphrase] [-f keyfile]
ssh-keygen -i [-m key_format] [-f input_keyfile]
ssh-keygen -e [-m key_format] [-f input_keyfile]
ssh-keygen -y [-f input_keyfile]
ssh-keygen -c [-P passphrase] [-C comment] [-f keyfile]
ssh-keygen -l [-v] [-E fingerprint_hash] [-f input_keyfile]
ssh-keygen -B [-f input_keyfile]
ssh-keygen -D pkcs11
ssh-keygen -F hostname [-f known_hosts_file] [-l]
ssh-keygen -H [-f known_hosts_file]
ssh-keygen -R hostname [-f known_hosts_file]
ssh-keygen -r hostname [-f input_keyfile] [-g]
ssh-keygen -G output_file [-v] [-b bits] [-M memory] [-S start_point]
ssh-keygen -T output_file -f input_file [-v] [-a rounds] [-J num_lines]
[-j start_line] [-K checkpt] [-W generator]
ssh-keygen -s ca_key -I certificate_identity [-h] [-n principals]
[-O option] [-V validity_interval] [-z serial_number] file ...
ssh-keygen -L [-f input_keyfile]
ssh-keygen -A
ssh-keygen -k -f krl_file [-u] [-s ca_public] [-z version_number]
file ...
ssh-keygen -Q -f krl_file file ...
[root@test02 ~]# ssh-keygen -t rsa '創建密鑰對 -t '
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:ZL4EmtVT8fXoCPScBgL7bldPv380zK93PQnA9kmORF8 root@test02
The key's randomart image is:
+---[RSA 2048]----+
| ... =. . |
| o + * o E |
| + = + B o .|
| + * . B = |
| o S o O * |
| o . o B =.|
| + . o.*|
| . . oB|
| .+*|
+----[SHA256]-----+
[root@test02 ~]# ls -a
. .bash_logout .dbus .ssh 圖片
.. .bash_profile .esd_auth .tcshrc 文檔
123123 .bashrc .ICEauthority .viminfo 桌面
123123.pub .cache initial-setup-ks.cfg .Xauthority 模板
anaconda-ks.cfg .config .local 下載 視頻
.bash_history .cshrc .mozilla 公共 音樂
[root@test02 ~]# cd .ssh
[root@test02 .ssh]# ls
id_rsa id_rsa.pub known_hosts
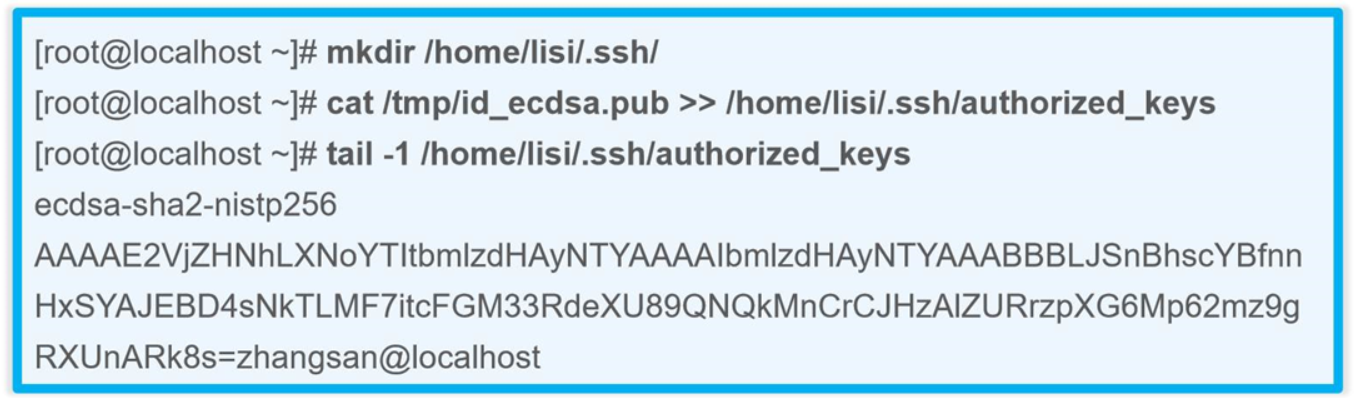
[root@test02 .ssh]# ssh-copy-id -i id_rsa.pub [email protected]
'複製密鑰對的公鑰複製到28服務端,以gsy身份'
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
[email protected]'s password: '輸入密碼'
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '[email protected]'"
and check to make sure that only the key(s) you wanted were added.
[root@test01 ~]# cd /home/gsy
[root@test01 gsy]# ls
下載 公共 圖片 文檔 桌面 模板 視頻 音樂
[root@test01 gsy]# ls -a
. .bash_logout .cache .ICEauthority .ssh 圖片 模板
.. .bash_profile .config .local 下載 文檔 視頻
.bash_history .bashrc .esd_auth .mozilla 公共 桌面 音樂
[root@test01 gsy]# cd .ssh
[root@test01 .ssh]# ls '驗證是否成功複製到28服務端'
authorized_keys
[root@test02 ~]# ssh [email protected] '再次遠程登陸服務端28'
Enter passphrase for key '/root/.ssh/id_rsa': '輸入之前輸入的密碼'
Last failed login: Wed Nov 20 20:17:55 CST 2019 from 192.168.139.129 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Wed Nov 20 18:51:51 2019 from 192.168.139.129
[gsy@test01 ~]$ '登陸成功'
[gsy@test01 ~]$ exit
logout
Connection to 192.168.139.128 closed.
[root@test02 ~]# ls -a
. .bash_logout .dbus .ssh 圖片
.. .bash_profile .esd_auth .tcshrc 文檔
123123 .bashrc .ICEauthority .viminfo 桌面
123123.pub .cache initial-setup-ks.cfg .Xauthority 模板
anaconda-ks.cfg .config .local 下載 視頻
.bash_history .cshrc .mozilla 公共 音樂
[root@test02 ~]# ls -a .ssh
. .. id_rsa id_rsa.pub known_hosts
[root@test02 ~]# ssh-agent bash '創建自動代理功能'
[root@test02 ~]# ssh-add '免交互'
Enter passphrase for /root/.ssh/id_rsa: '輸入密碼確認'
Identity added: /root/.ssh/id_rsa (/root/.ssh/id_rsa)
[root@test02 ~]#
[root@test02 ~]# ssh [email protected] '再次以gsy身份去登陸28服務端'
Last login: Wed Nov 20 21:33:22 2019 from 192.168.139.130 '網絡被切換,客戶機IP地址改變'
ssh-agent bash 創建自動代理功能
ssh-add 免交互
可以用於在shelle腳本遠程
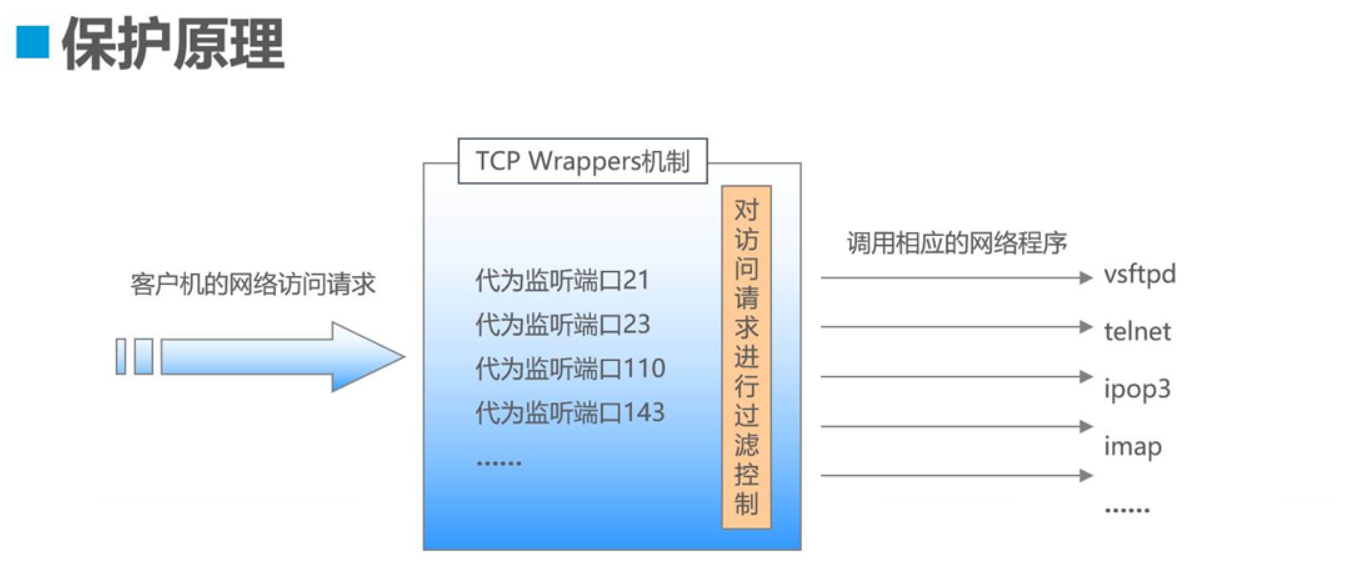
四 :TCP Wrappers 概述
4.1 保護機制的實現方式
- 方式1 : 通過tcpd主程序對其他服務程序進行包裝
- 方式2 : 有其他服務程序調用libwrap.so.*鏈接庫
4.2 訪問控制策略的配置文件
- /etc/hosts.allow
- /etc/hosts.deny
其中,ssh就是能夠被它管控的服務
[root@test01 .ssh]# ldd `which sshd`
linux-vdso.so.1 => (0x00007ffd5eb16000)
libfipscheck.so.1 => /lib64/libfipscheck.so.1 (0x00007f4e20f2b000)
libwrap.so.0 => /lib64/libwrap.so.0 (0x00007f4e20d20000)
libaudit.so.1 => /lib64/libaudit.so.1 (0x00007f4e20af7000)
libpam.so.0 => /lib64/libpam.so.0 (0x00007f4e208e8000)
libselinux.so.1 => /lib64/libselinux.so.1 (0x00007f4e206c1000)
libsystemd.so.0 => /lib64/libsystemd.so.0 (0x00007f4e20698000)
libcrypto.so.10 => /lib64/libcrypto.so.10 (0x00007f4e20237000)
libdl.so.2 => /lib64/libdl.so.2 (0x00007f4e20033000)
libldap-2.4.so.2 => /lib64/libldap-2.4.so.2 (0x00007f4e1fdde000)
liblber-2.4.so.2 => /lib64/liblber-2.4.so.2 (0x00007f4e1fbcf000)
libutil.so.1 => /lib64/libutil.so.1 (0x00007f4e1f9cc000)
libz.so.1 => /lib64/libz.so.1 (0x00007f4e1f75000)
libcrypt.so.1 => /lib64/libcrypt.so.1 (0x00007f4e1f57e000)
libresolv.so.2 => /lib64/libresolv.so.2 (0x00007f4e1f364000)
libgssapi_krb5.so.2 => /lib64/libgssapi_krb5.so.2 (0x00007f4e1f116000)
libkrb5.so.3 => /lib64/libkrb5.so.3 (0x00007f4e1ee2e000)
libk5crypto.so.3 => /lib64/libk5crypto.so.3 (0x00007f4e1ebfb000)
libcom_err.so.2 => /lib64/libcom_err.so.2 (0x00007f4e1e9f6000)
libc.so.6 => /lib64/libc.so.6 (0x00007f4e1e633000)
libnsl.so.1 => /lib64/libnsl.so.1 (0x00007f4e1e41a000)
libcap-ng.so.0 => /lib64/libcap-ng.so.0 (0x00007f4e1e213000)
libpcre.so.1 => /lib64/libpcre.so.1 (0x00007f4e1dfb1000)
/lib64/ld-linux-x86-64.so.2 (0x0000562f68c55000)
libcap.so.2 => /lib64/libcap.so.2 (0x00007f4e1ddac000)
libm.so.6 => /lib64/libm.so.6 (0x00007f4e1daa9000)
librt.so.1 => /lib64/librt.so.1 (0x00007f4e1d8a1000)
liblzma.so.5 => /lib64/liblzma.so.5 (0x00007f4e1d67b000)
libgcrypt.so.11 => /lib64/libgcrypt.so.11 (0x00007f4e1d3f9000)
libgpg-error.so.0 => /lib64/libgpg-error.so.0 (0x00007f4e1d1f4000)
libdw.so.1 => /lib64/libdw.so.1 (0x00007f4e1cfad000)
libgcc_s.so.1 => /lib64/libgcc_s.so.1 (0x00007f4e1cd96000)
libpthread.so.0 => /lib64/libpthread.so.0 (0x00007f4e1cb7a000)
libsasl2.so.3 => /lib64/libsasl2.so.3 (0x00007f4e1c95d000)
libssl3.so => /lib64/libssl3.so (0x00007f4e1c710000)
libsmime3.so => /lib64/libsmime3.so (0x00007f4e1c4e9000)
libnss3.so => /lib64/libnss3.so (0x00007f4e1c1bf000)
libnssutil3.so => /lib64/libnssutil3.so (0x00007f4e1bf91000)
libplds4.so => /lib64/libplds4.so (0x00007f4e1bd8d000)
libplc4.so => /lib64/libplc4.so (0x00007f4e1bb88000)
libnspr4.so => /lib64/libnspr4.so (0x00007f4e1b949000)
libfreebl3.so => /lib64/libfreebl3.so (0x00007f4e1b746000)
libkrb5support.so.0 => /lib64/libkrb5support.so.0 (0x00007f4e1b537000)
libkeyutils.so.1 => /lib64/libkeyutils.so.1 (0x00007f4e1b333000)
libattr.so.1 => /lib64/libattr.so.1 (0x00007f4e1b12d000)
libelf.so.1 => /lib64/libelf.so.1 (0x00007f4e1af15000)
libbz2.so.1 => /lib64/libbz2.so.1 (0x00007f4e1ad04000)
查詢功能模塊 `後面接命令
五 : TCP Wrappers 策略應用
5.1 設置訪問控制策略
- 策略格式 : 服務列表:客戶機地址列表
- 服務列表
- 多個服務以逗號分隔,ALL表示所有服務
- 客戶機地址列表
- 多個地址以逗號分隔,ALL表示所有地址
- 允許使用通配符?和*
- 網段地址,如192.168.4. 或者192.168.4.0/255.255.255.0
- 區域地址,如 .bennet,com
5.2 策略的應用順序
- 先檢查hosts.allow,找到匹配則允許訪問
- 否則再檢查hosts.deny,找到則拒絕訪問
- 若兩個文件中均無匹配策略,則默認允許訪問
- 禁止其他所有地址訪問受保護的服務
[root@localhost ~]# echo "sshd:61.63.65.67,192.168.2.*" > /etc/hosts.allow
[root@localhost ~]# vi /etc/hosts.allow
sshd:61.63.65.67,192.168.2.*
[root@localhost ~]# echo "sshd:ALL" > /etc/hosts.deny
[root@localhost ~]# vi /etc/hosts.deny
sshd:ALL
[root@localhost ~]#
優先讀取allow,然後再度deny
如果只想禁止某些主機登陸,則只做黑名單,白名單不寫
小結:
ssh 22端口
服務端配置文件 /etc/ssh/sshd_config
Port 22 '端口號'
ListenAddress 192.168.155.155 '監聽地址'
Protocol 2 '版本號'
UserDNS no 'DNS反向解析,否'
LoginGraceTime 2m '登陸時間 2m'
PermitRootLogin no '允許root登陸 否'
MaxAuthTries 6 '最大嘗試登陸次數 6 次'
PermitEmptyPasswords no '禁止空密碼'
AllowUsers gsy [email protected]
'只允許gsy登陸,lisi從192.168.88.88登陸,別人都不行'
PasswordAuthentication yes '需要密碼驗證 是'
PubkeyAuthentication yes '開啓密鑰對驗證 是'
AuthorizedKeyFile .ssh/authorized_keys '密鑰對文件位置'遠程登陸
ssh 用戶名@ip地址 -p 指定端口號
遠程複製
scp 要複製的文件 複製到的目標位置
scp 用戶名@ipdizhi:源文件路徑 目標路徑
遠程上下載
sftp 用戶名@ip地址
ssh中構建密鑰對
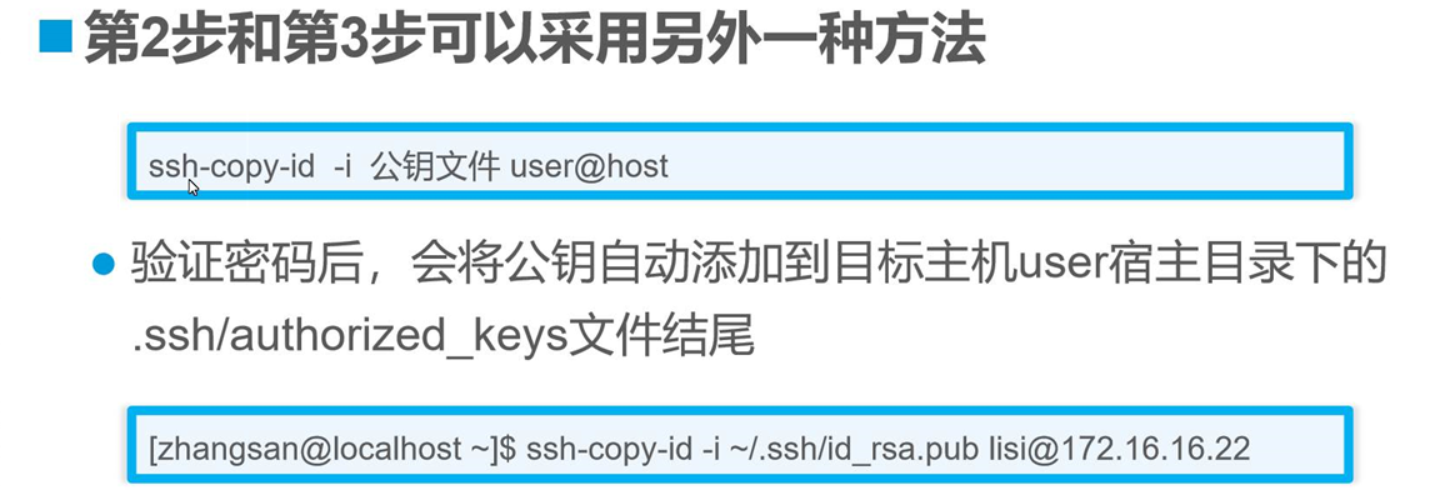
ssh-keygen -t rsa(或dsa算法) 創建密鑰對
ssh-copy -i 公鑰文件路徑 用戶名@目標ip地址
ssh-copy -i ~/.ssh/id_rsa.pub [email protected]
ssh-agent bash 創建自動代理功能
ssh-add 免交互
TCP Wrappers 保護主程序
ldd ·which sshd·
訪問控制策略的配置文件
/etc/hosts.allow
/etc/hosts.deny
如果做黑名單,白名單可以不寫